Enable Your First Policy Pack
Enable Your First Policy Pack
In this guide, you will learn how to attach a Guardrails Policy Pack to enable governance controls.
This is the fourth guide in the Getting started with AWS series.
Prerequisites
- Completion of the previous guides in this series.
- Access to the Guardrails console with administrative privileges.
- Access to AWS console with the ability to create and modify S3 buckets.
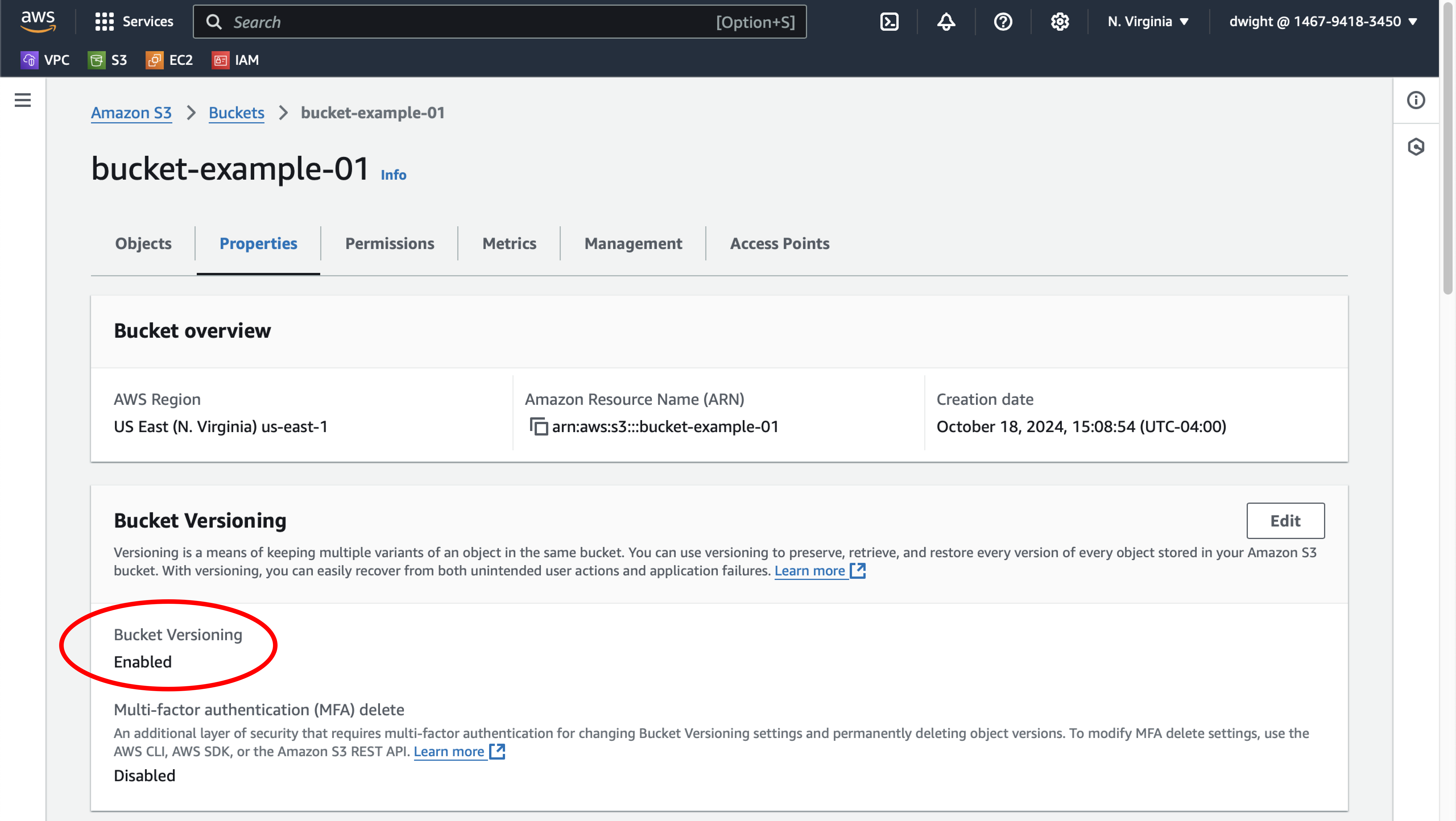
Step 1: Check bucket versioning in AWS
Check the properties of the bucket you created in the previous guide (Observe AWS activity). Verify that versioning is still enabled on the test bucket you created.
Step 2: Filter controls
You bookmarked the Controls by State report in the Connect an Account guide, go there now. From the filter bar open the Type dropdown and search for aws s3 bucket versioning. Select the checkbox next to AWS > S3 > Bucket > Versioning.

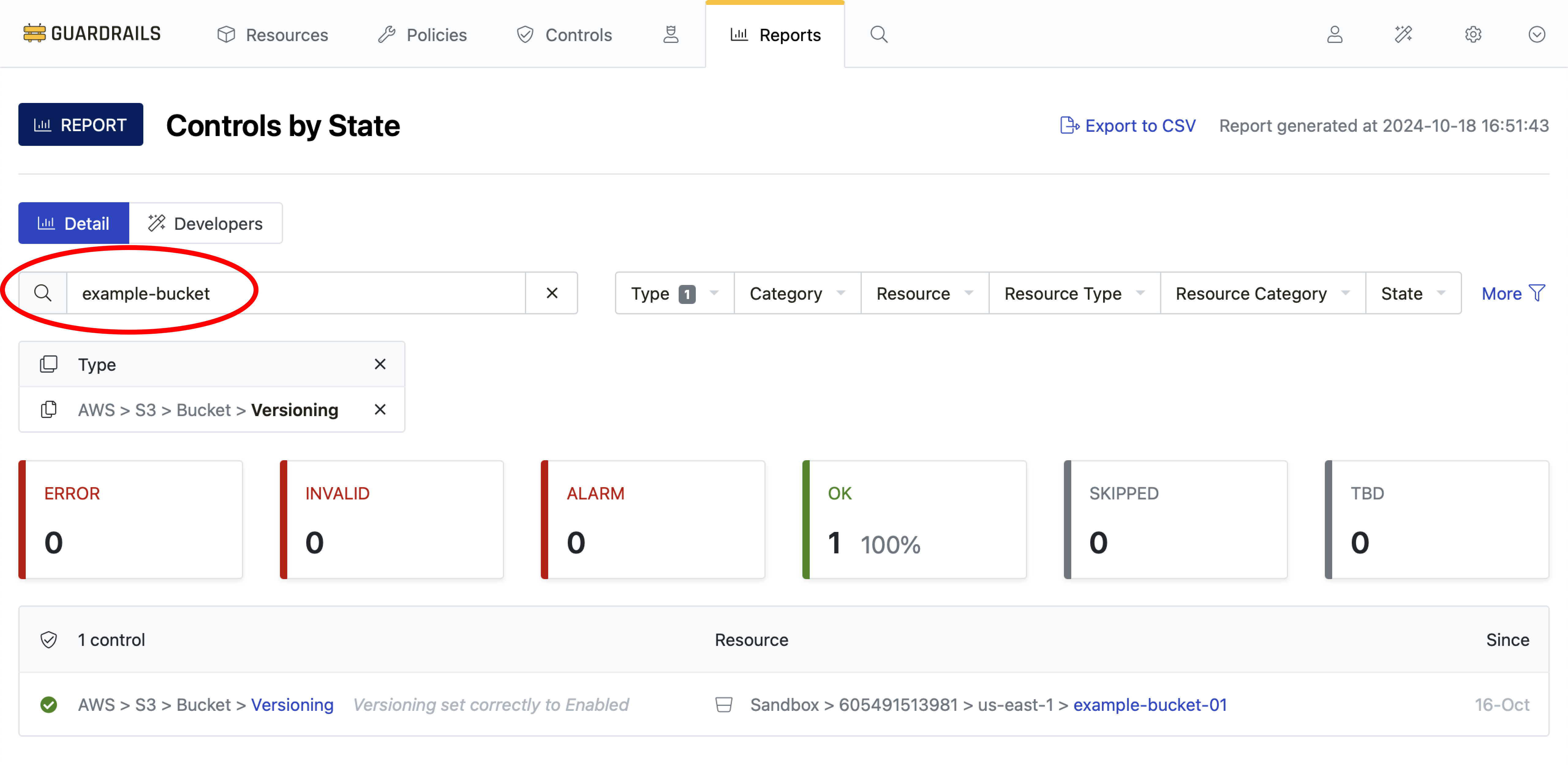
Step 3: Find your bucket
Search for your bucket by typing its name into the search field. It should be in the Skipped state, because Guardrails has not been configured to check bucket versioning.
Update your bookmark with this new filtered view.
Step 4: Navigate to your account
Control-click on the Guardrails logo on the top of the page to open a new homepage browser tab.
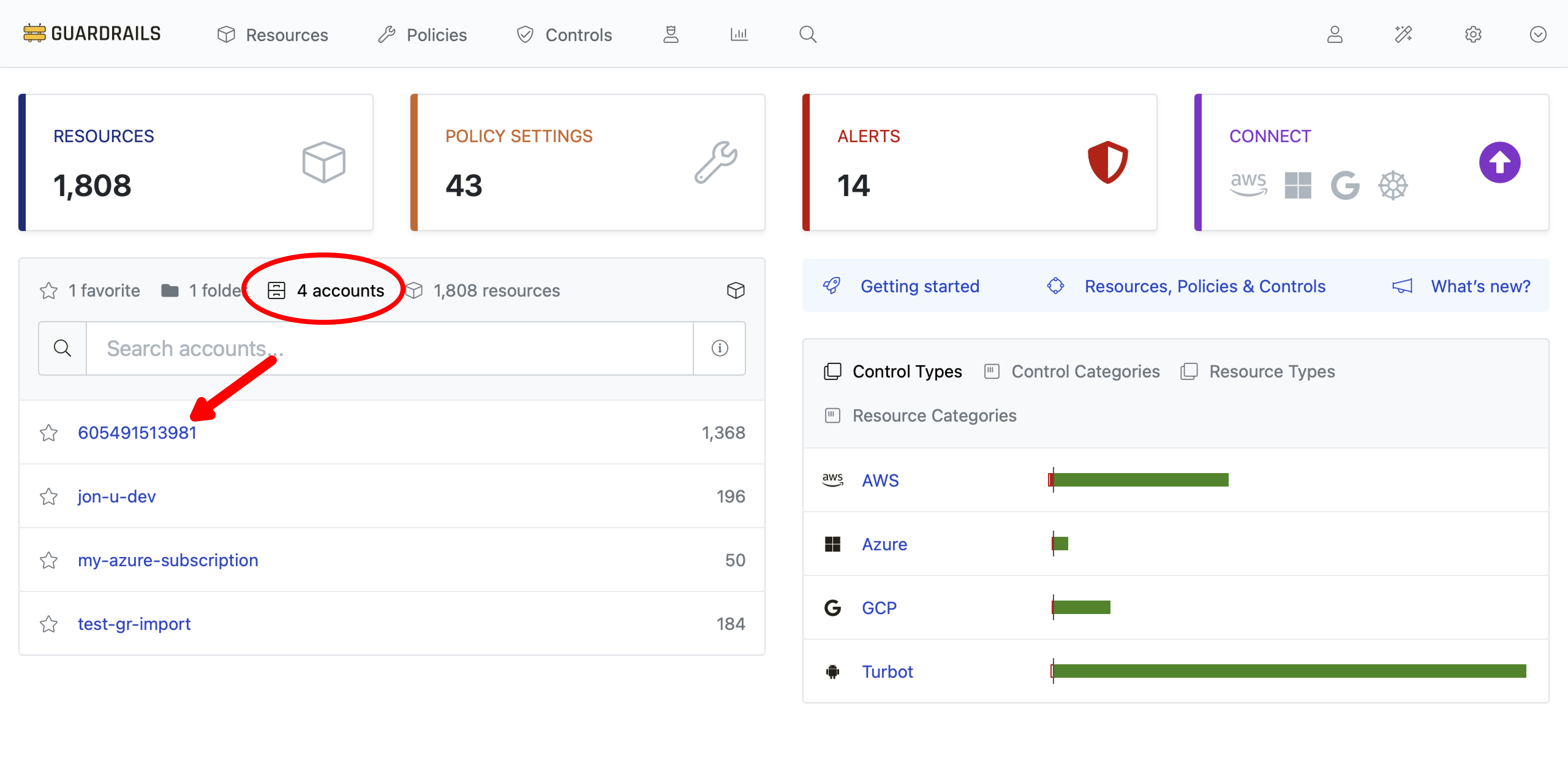
Click on the Accounts sub-tab from the homepage and then select the AWS account you are using for testing from the list.
On the account resource page, select the Detail sub-tab.
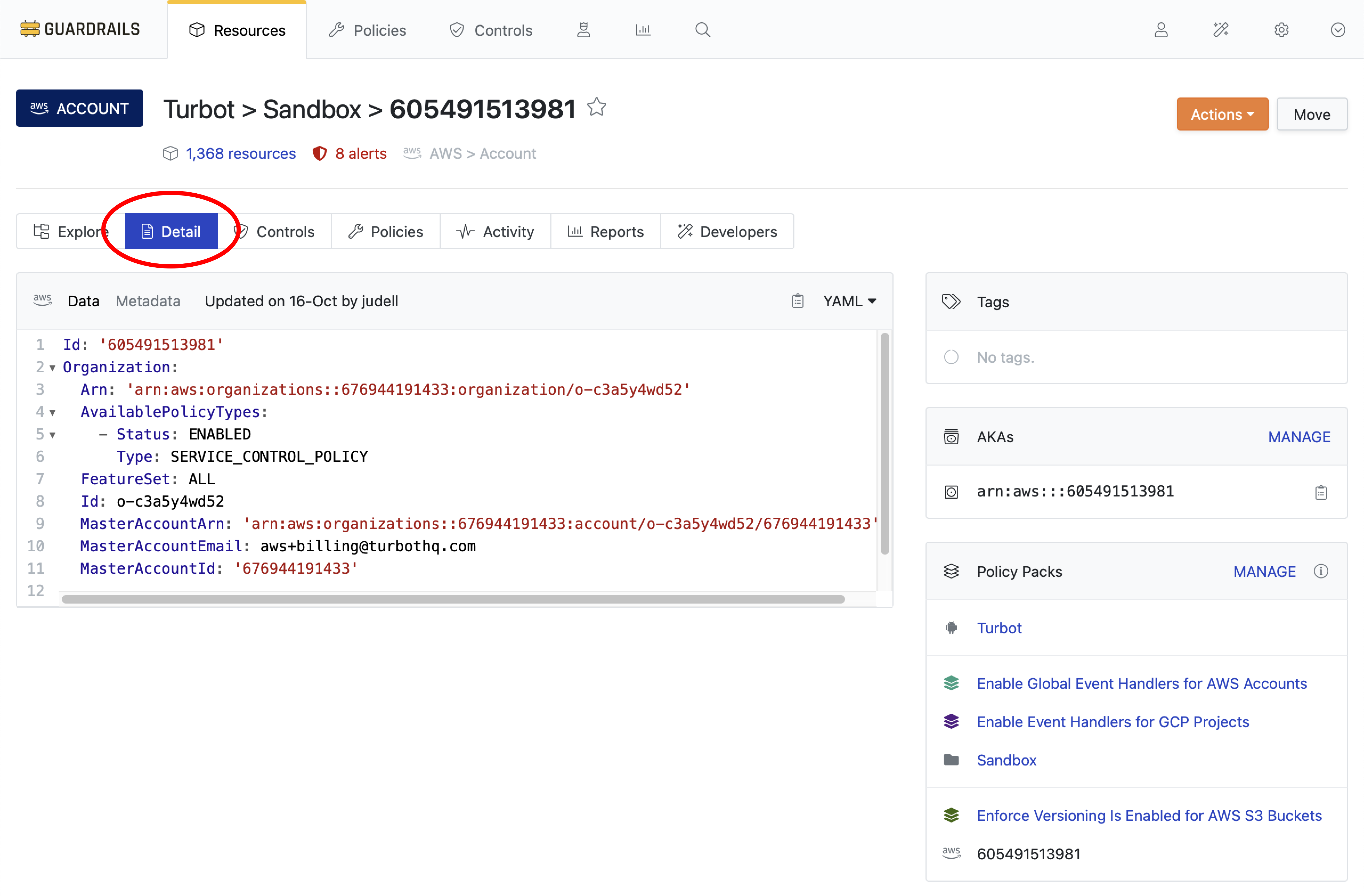
Step 5: Locate the Policy Pack manager
Select the Manage Link next to Policy Packs UI widget.
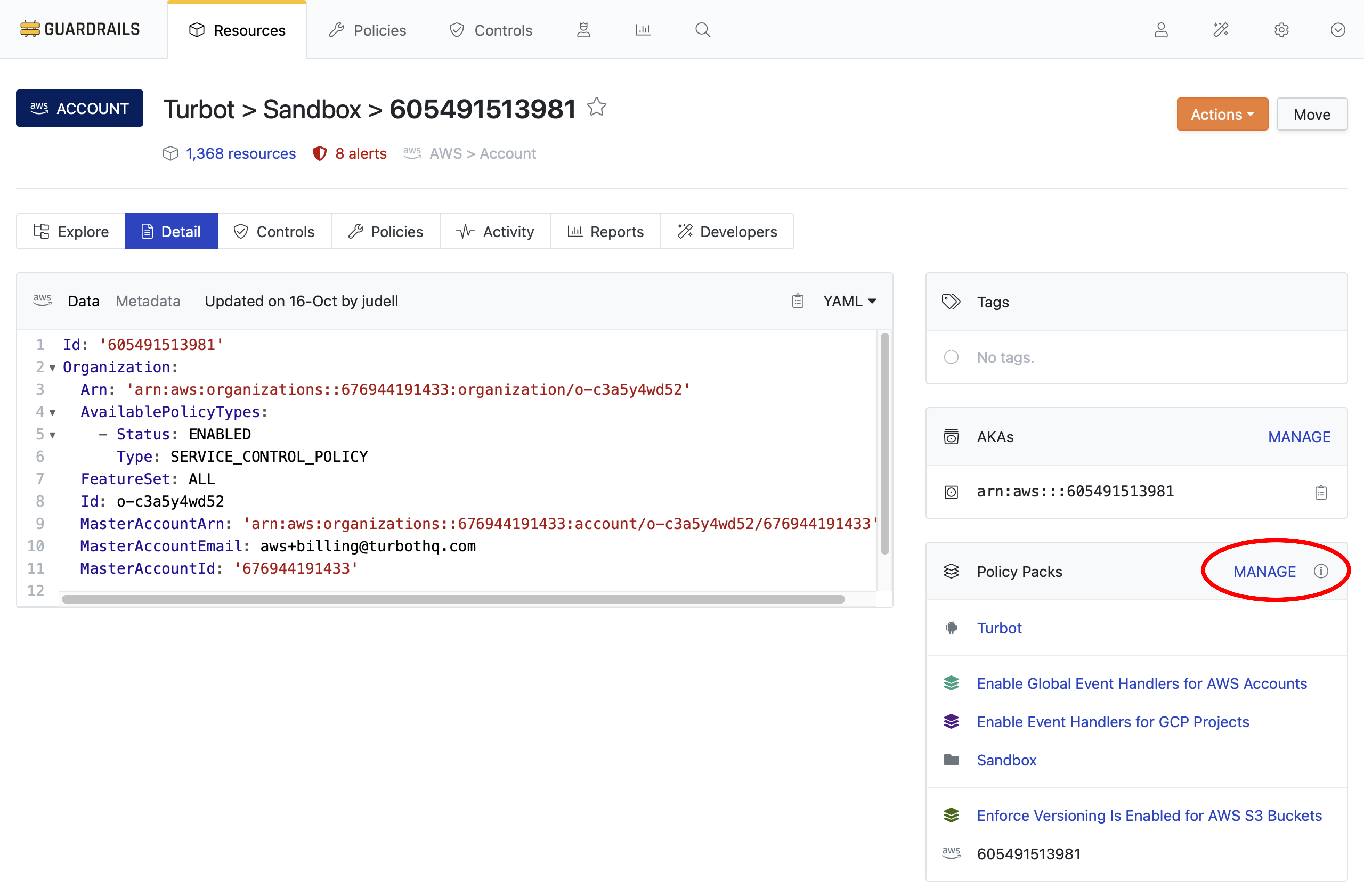
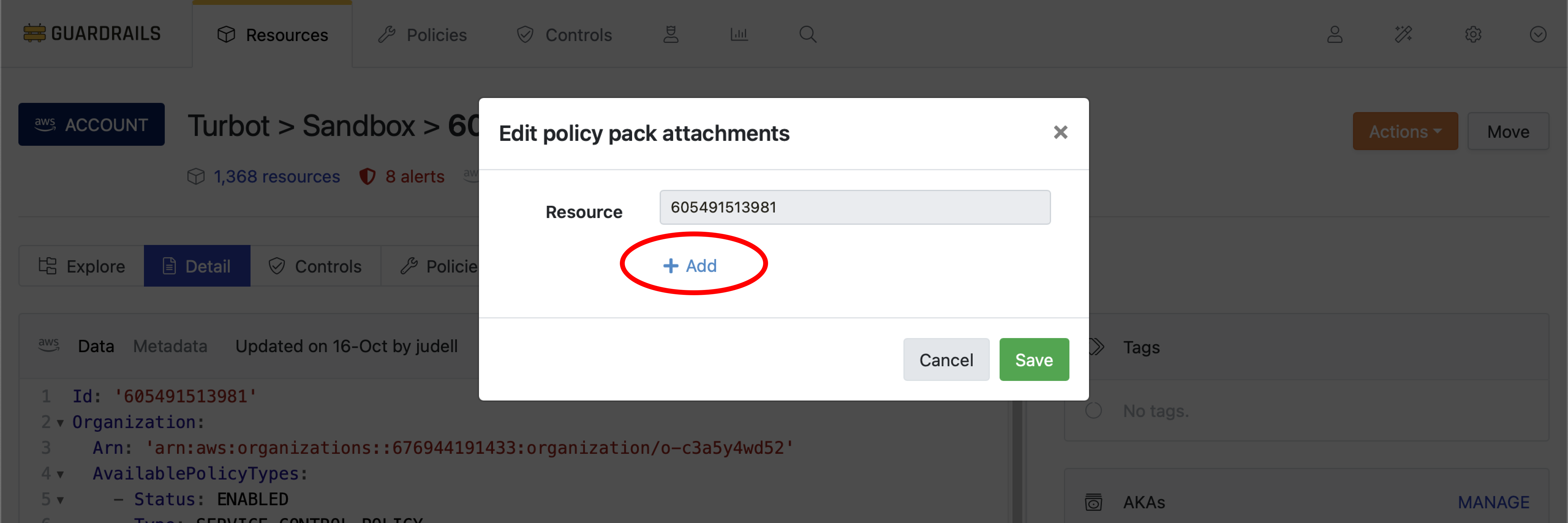
Step 6: Attach the Policy Pack to your account
In the Edit policy pack attachments dialog box, select Add.
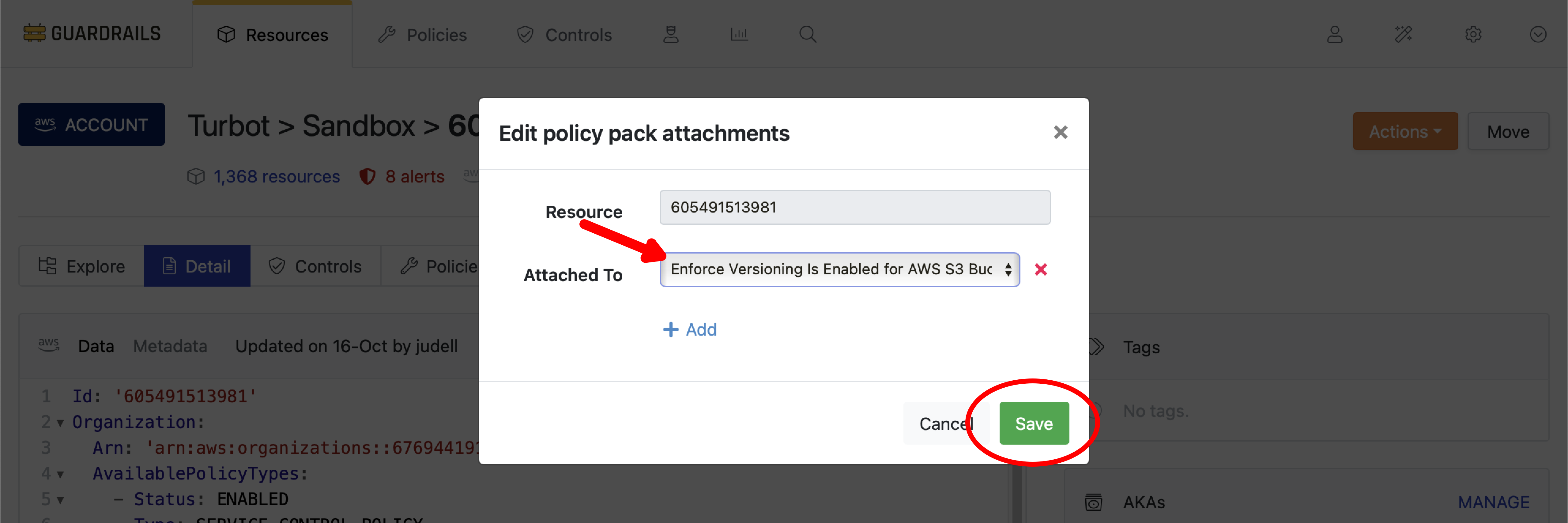
Your Guardrails workspace should have the Policy Pack Enforce Versioning Is Enabled for AWS S3 Buckets pre-installed.
In the dropdown, select the Policy Pack named Enforce Versioning is Enabled for AWS S3 Buckets. Then select Save.
Step 7: Observe policy effect
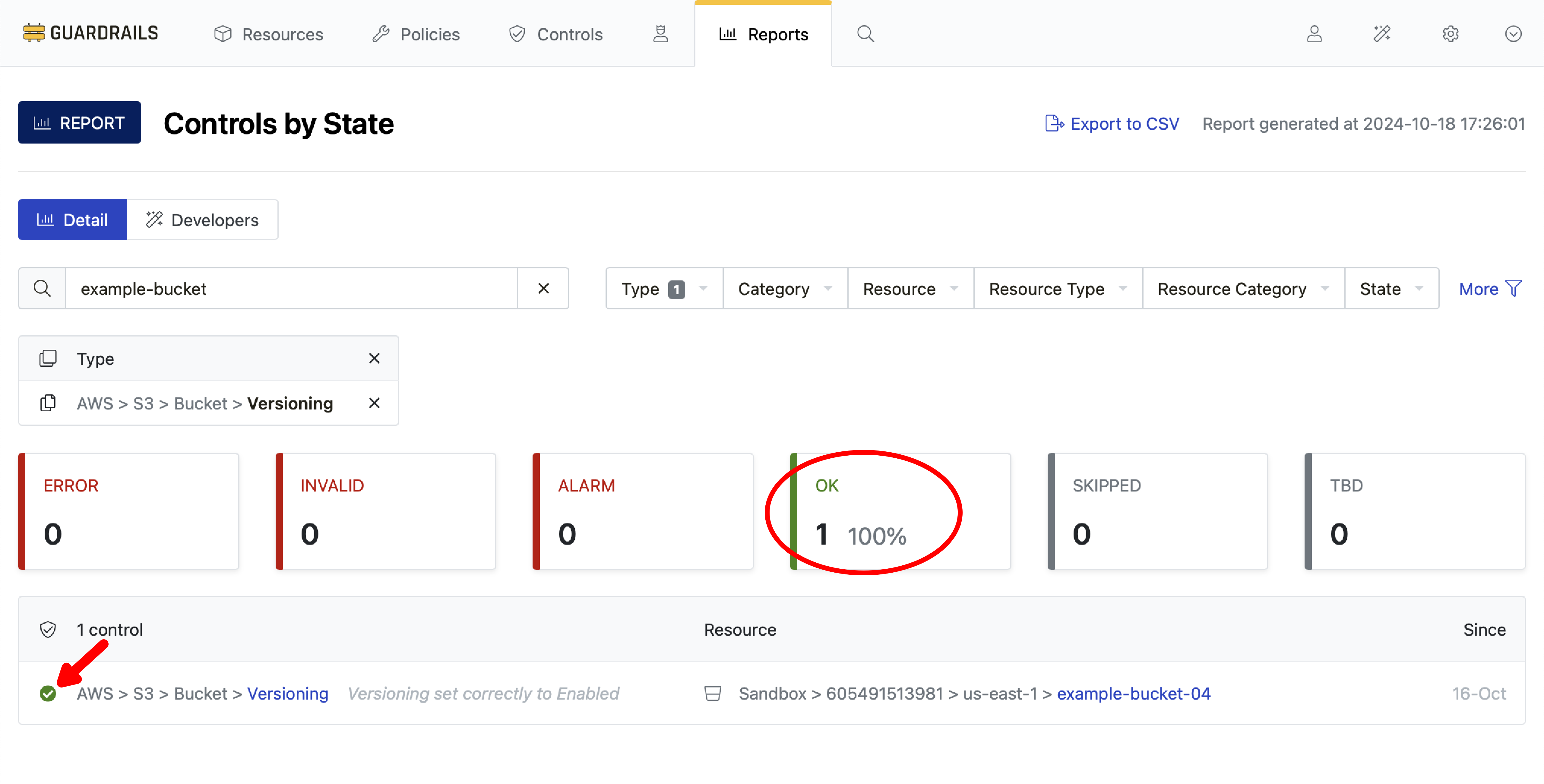
Return to your open browser tab (or bookmark) for the Controls by State report. Observe that the control state for your test bucket changes from Skip to Ok. It is in Ok state because the policy pack you added has enabled the control to test for that condition.
Step 8: Review
In this guide you’ve attached a Policy Pack to your AWS account to check S3 bucket versioning, and observed how the policy affects the Versioning control for your S3 bucket.
Next Steps
In the next guide you will create some additional buckets to see how the Policy Pack responds to new resource creation.
Progress tracker
- [x] Prepare an AWS Account for Import to Guardrails
- [x] Connect an AWS Account to Guardrails
- [x] Observe AWS Resource Activity
- [x] Enable Your First Policy Pack
- [ ] Review Account-Wide Governance
- [ ] Create a Static Exception to a Guardrails Policy
- [ ] Create a Calculated Exception to a Guardrails Policy
- [ ] Send an Alert to Email
- [ ] Apply a Quick Action
- [ ] Enable Automatic Enforcement