{ "Version": "2012-10-17", "Statement": [ { "Sid": "DenyRegionRestriction", "Effect": "Deny", "NotAction": [ "a4b:*", "acm:*", "aws-marketplace:*", "aws-portal:*", "budgets:*", "ce:*", "cloudfront:*", "config:*", "ec2:DescribeRegions" // ... 150+ more services ... ], "Resource": "*", "Condition": { "StringNotEquals": { "aws:RequestedRegion": ["us-east-1", "us-west-2"] } } ...Native Preventive Controls Are Complex
AWS SCPs, Azure Policies, GCP Org Policies - powerful controls, but understanding what they actually do is difficult. One policy might contain 50 statements with nested conditions. Your org might have 20 policies attached at different levels.
With 100 accounts, the effective permissions become nearly impossible to compute. Getting answers means opening policy JSON in one tab, navigating OUs in another, and mentally computing policy intersections.
Security teams need answers:
- Which regions can production accounts deploy to?
- What services are restricted in development?
- Where do multiple policies conflict?
- Which accounts have exceptions granted months ago?
Visualize your preventive controls across all accounts:
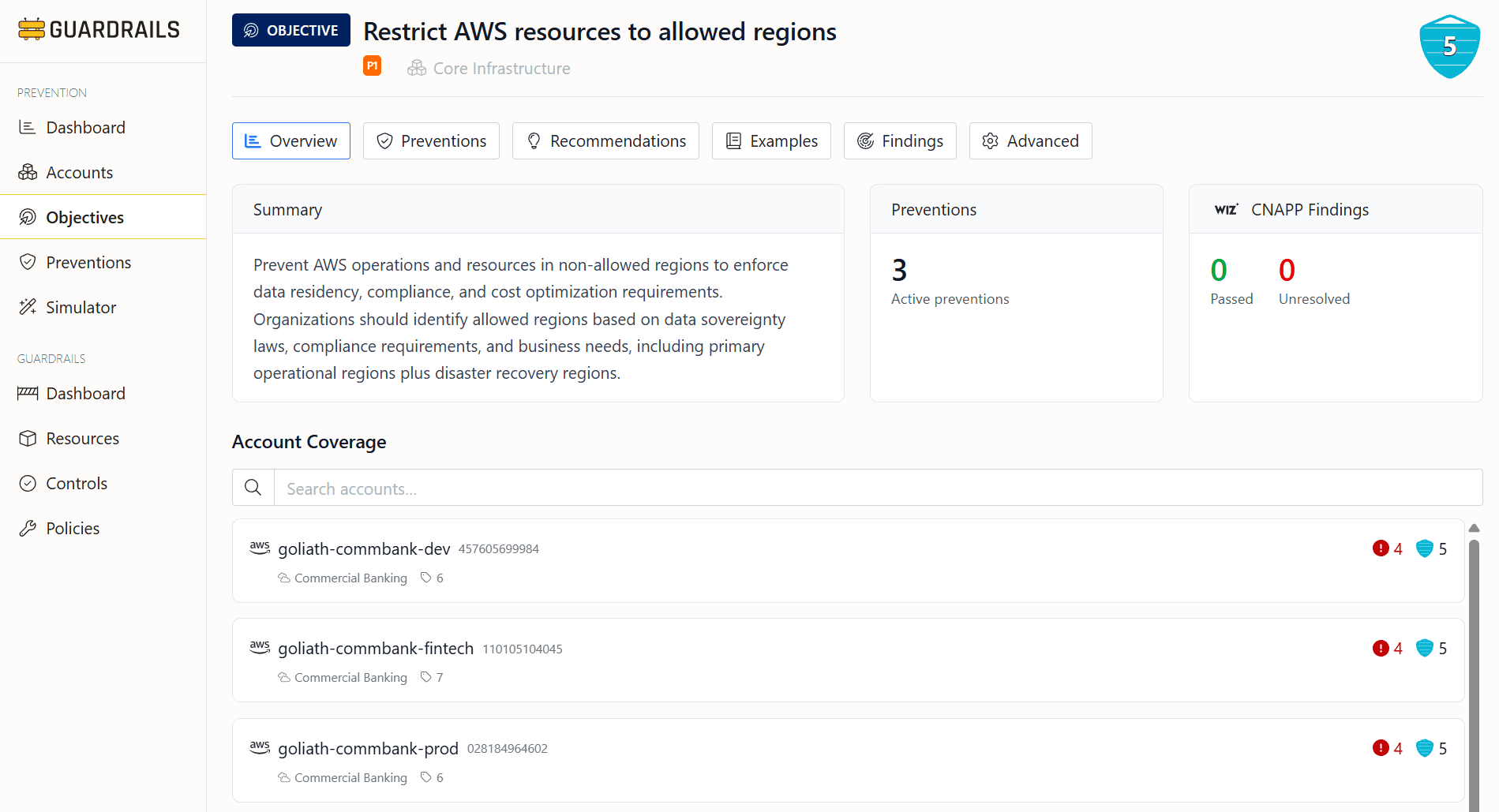
Prevention Objectives
Guardrails organizes preventive controls around security objectives. Each objective represents a specific security goal - restricting resources to approved regions, preventing public S3 buckets, requiring encrypted volumes.
Objectives have priorities (P1 essential through P5 hygiene) and categories (Core Infrastructure, Data Governance, Identity & Access).
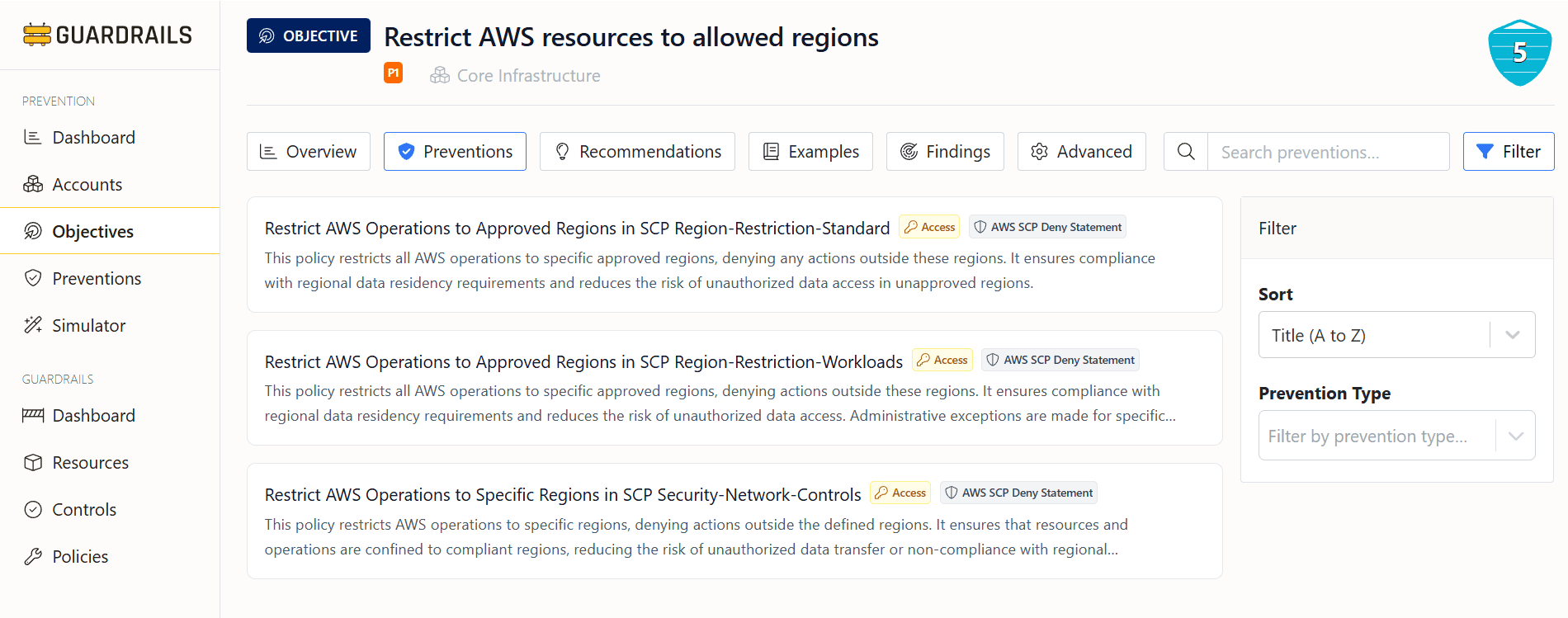
Prevention Rules
Guardrails discovers every preventive control in your environment: AWS SCPs, Control Tower controls, Resource Control Policies, Azure Policies, GCP Org Policies, GitHub organization policies, CloudFormation hooks, and account-level defaults.
Each discovered policy becomes a prevention rule with plain language translation.

Policy Relationship Graph
View your entire organizational hierarchy with policy attachments, inheritance chains, and blast radius. See where each policy is attached - Root, OU, or specific accounts.
Search for specific policies and the graph highlights the related SCPs and the accounts they protect. The visual layout makes inheritance and blast radius clear.
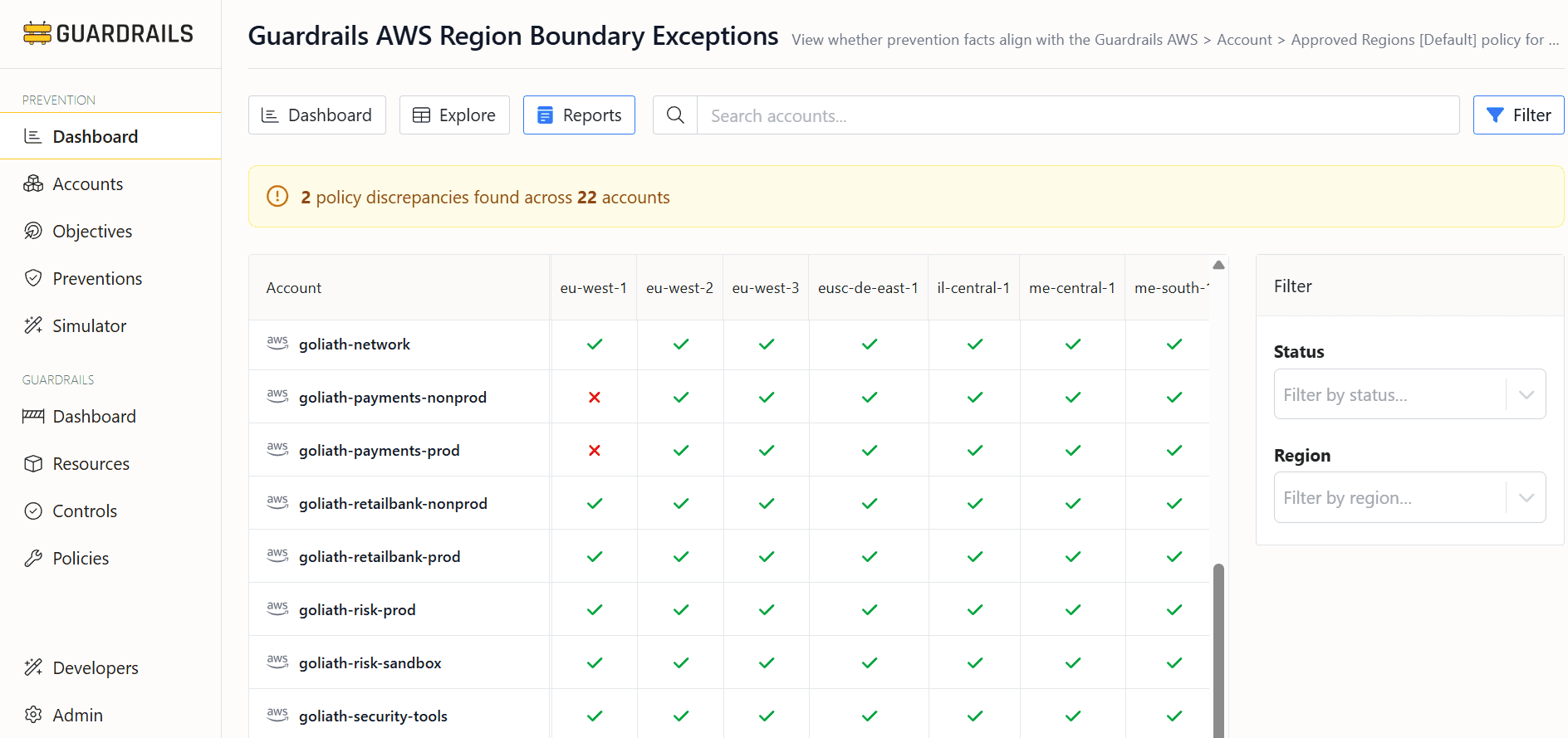
Interactive Reports
Visualize preventive control posture across all accounts. Reports surface the exceptions and anomalies that stay hidden in policy JSON - the temporary exception granted 18 months ago, accounts with conflicting inherited policies, gaps where controls should exist.
Search, filter by status and region. Export for compliance evidence.