Connect an AWS Account to Guardrails
Connect an AWS Account to Guardrails
In this guide, you will deploy the Guardrails IAM access role to your AWS account using a CloudFormation template and then connect that account to Guardrails.
This is the second guide in the Getting started with AWS series.
Prerequisites
- Completed the previous guide: Prepare an AWS Account for import to Guardrails.
- Access to the Turbot Guardrails console with admin privilege.
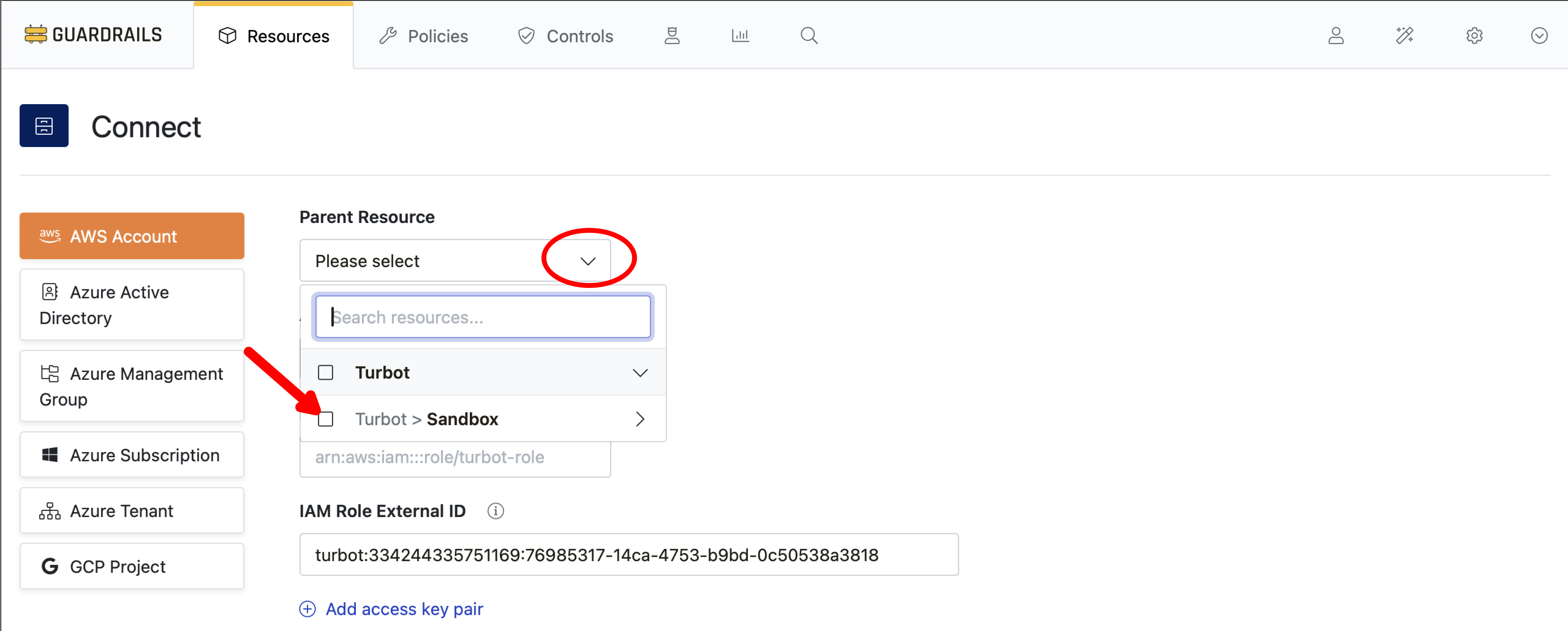
Step 1: Select import location
Switch back to the Guardrails console Account Import browser tab you opened in the previous guide. Use the Parent Resource dropdown to select the Sandbox folder as the location to import the account.
Note: If the Sandbox folder does not exist in your workspace, you’ll need to create one.
This folder is commonly used for testing, isolation, or non-production accounts.
Refer to the Create Folder Guide for steps on how to create a folder in Guardrails.
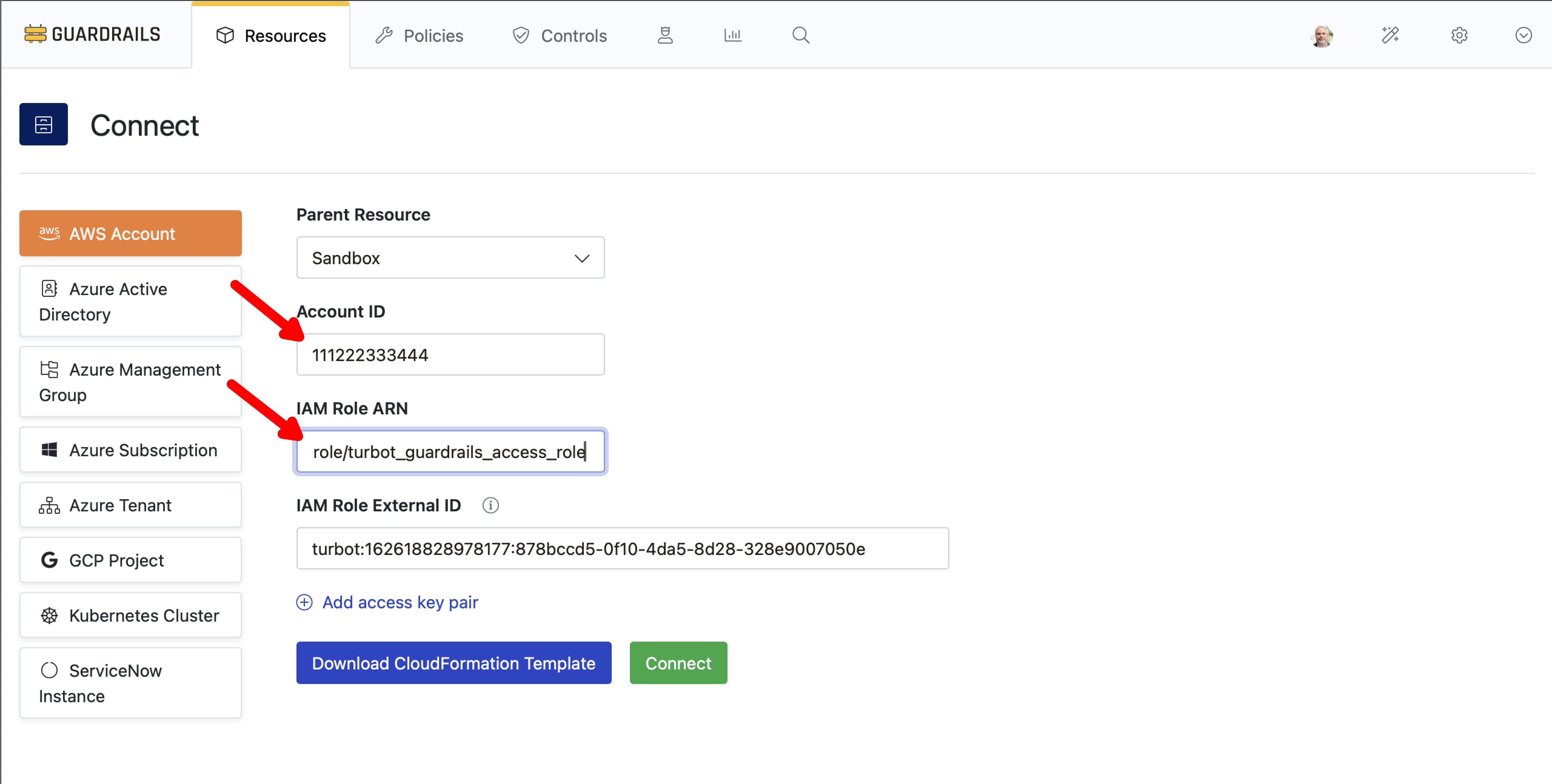
Step 2: Update account details
Paste the role ARN you obtained from step 7 in the previous guide into the IAM Role ARN field and enter the AWS account ID into the Account ID field.
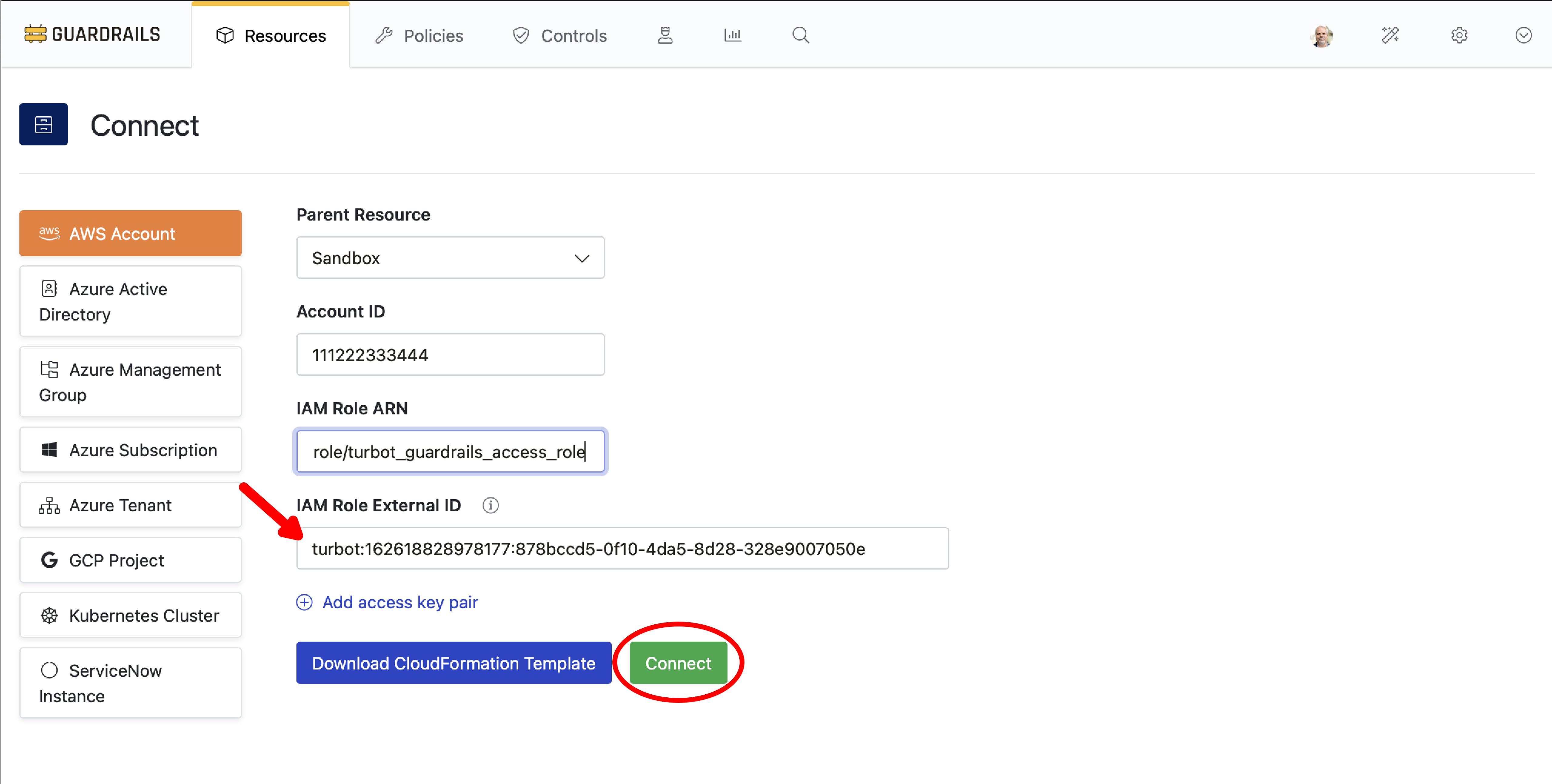
Step 3: Import the account
Triple-check that the IAM Role External ID matches the value from the CloudFormation template. If not, overwrite the current value with the one from the Cloudformation output. Select Connect to import your account.
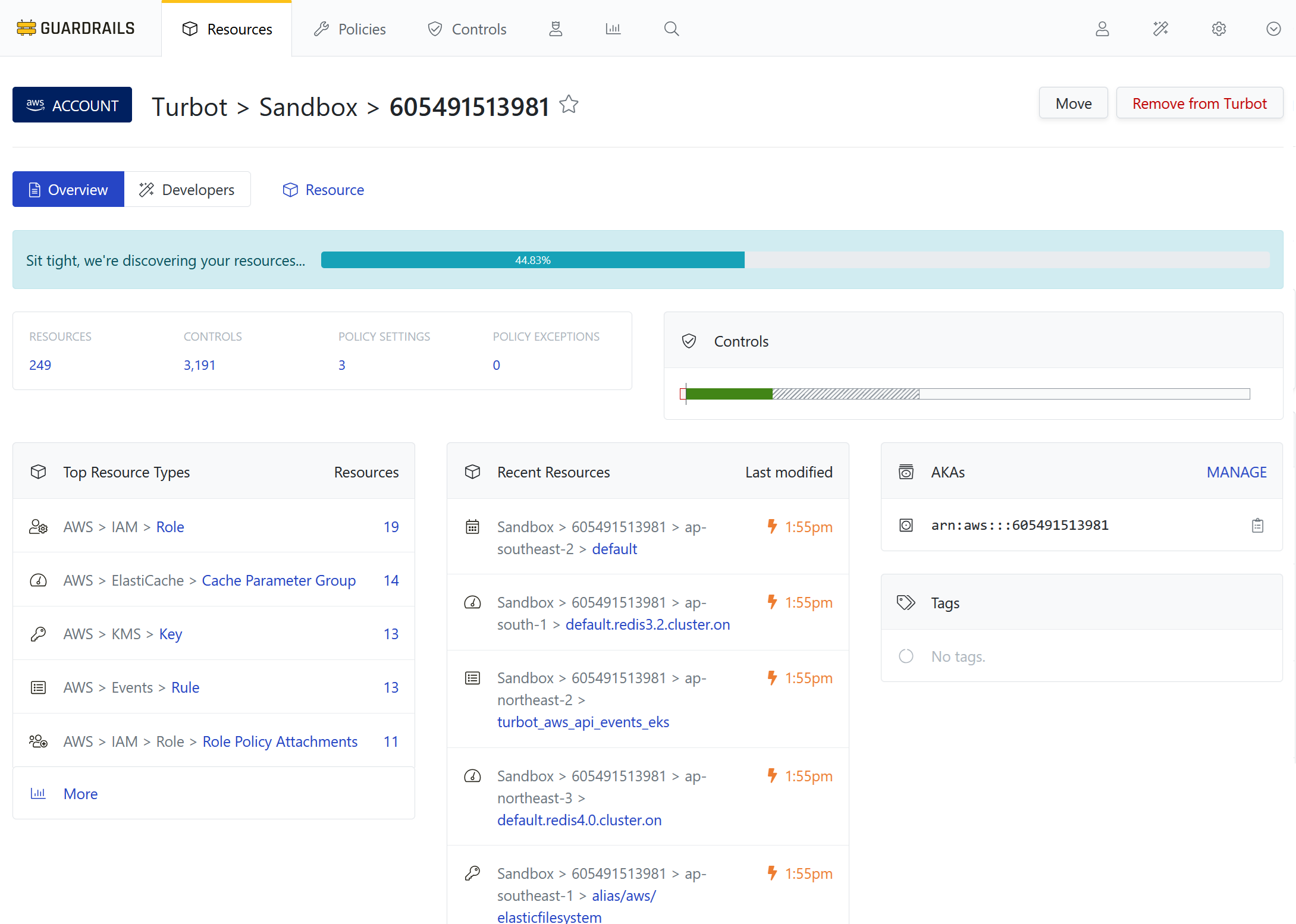
Step 4: Observe progress
Wait for the progress bar to complete. The time this takes will depend on how many resources are in the account; it is normal for the progress bar to fluctuate in size as new types of resources are discovered.
Step 5: View Controls by state
Select Reports from the top navigation menu. Type controls into the Search reports… field to show only reports with the word "controls" in their name. Select the Controls by State report from the list.
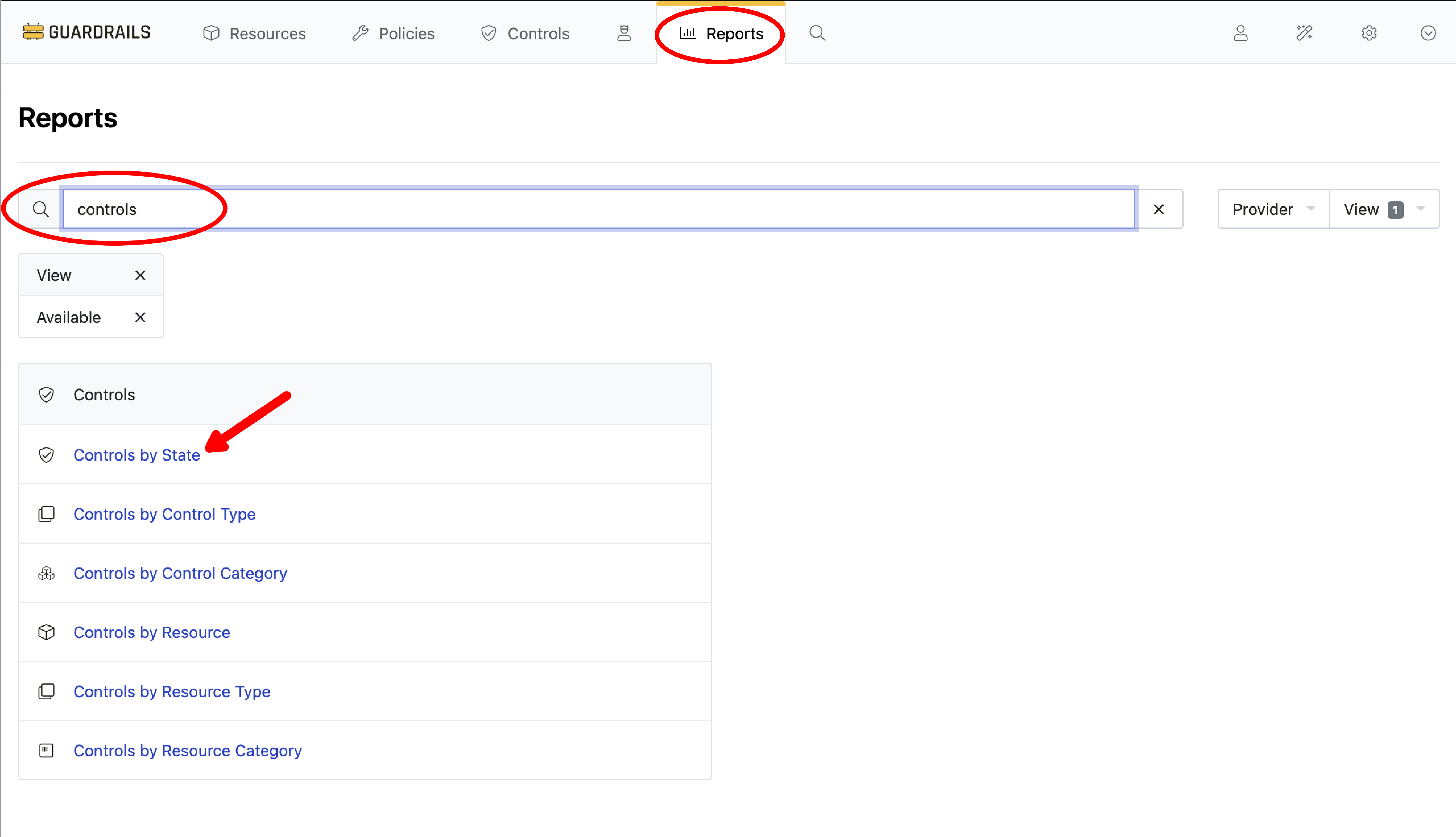
Step 6: Configure report filters
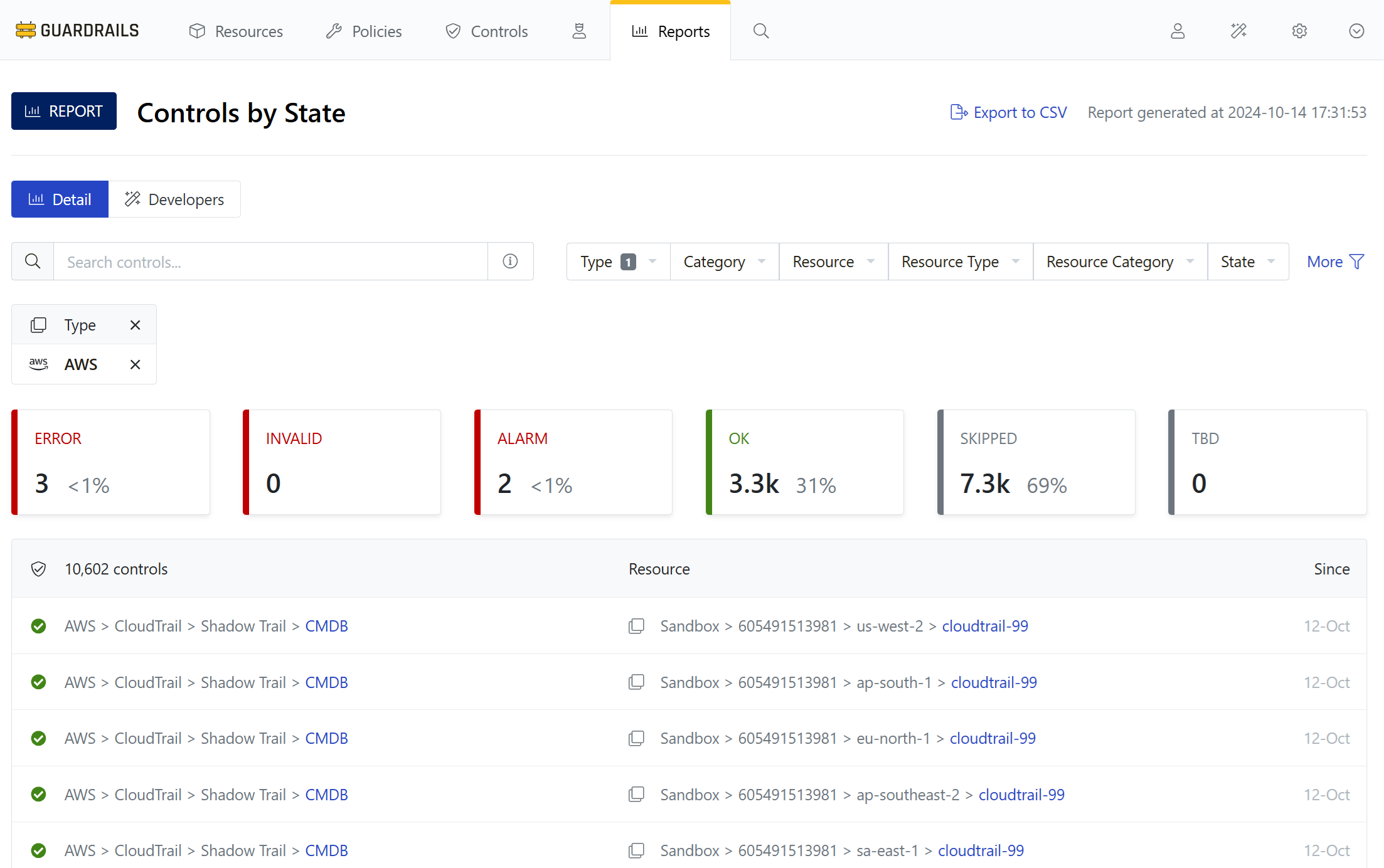
From the filter bar, expand the Type dropdown. Then select the checkbox next to AWS to limit the report to only show AWS controls.
Bookmark the Controls by State report, you’ll need it in subsequent guides.

Step 7: View the report
Review the status of your controls for AWS. Alarm, OK, Skipped, and TBD are all common and normal states to see in your account.
[!IMPORTANT] The controls in
ErrororInvalidstates must be cleared before moving further into these guides. It takes few mins depending on various factors. We suggest to wait and report to Turbot support, in case these errors are not cleared up automatically.
Step 8: Review
In this guide you successfully imported an AWS account into Guardrails.
Next Steps
In the next guide we’ll see how Guardrails monitors cloud events and reacts to resource changes.
Troubleshooting
If you run into issues following this guide, jump in the #guardrails channel in the Turbot Community Slack, or open a support ticket.
Progress tracker
- [x] Prepare an AWS Account for Import to Guardrails
- [x] Connect an AWS Account to Guardrails
- [ ] Observe AWS Resource Activity
- [ ] Enable Your First Policy Pack
- [ ] Review Account-Wide Governance
- [ ] Create a Static Exception to a Guardrails Policy
- [ ] Create a Calculated Exception to a Guardrails Policy
- [ ] Send an Alert to Email
- [ ] Apply a Quick Action
- [ ] Enable Automatic Enforcement