We are often asked by potential customers how Turbot Guardrails can help implement and enforce policies to avoid accidental (or malicious) exposure of data in S3. While best practices to accomplish this are well known, ensuring and executing these best practices at scale require automation.
For many large organizations, the benefits and capabilities of public cloud often lead to exponential growth of IT services. Organizations frequently find that their initial operations processes (designed for a handful of applications) become resource constrained when scaled to 100s, or 1000s of workloads. The challenge for your Cloud Team is how to ensure all workloads and data are protected per company policies and best practices as your environment scales up.
Turbot Guardrails provides 20+ out-of-the-box options and policies for securely managing AWS S3. Our current customers use these guardrails to correctly configure buckets and lockdown IAM privileges; preventing misconfiguration that could lead to confidential data being exposed.Turbot Guardrails combination of preventative and corrective controls ensures that buckets are configured to best practices initially, and stay that way over time.
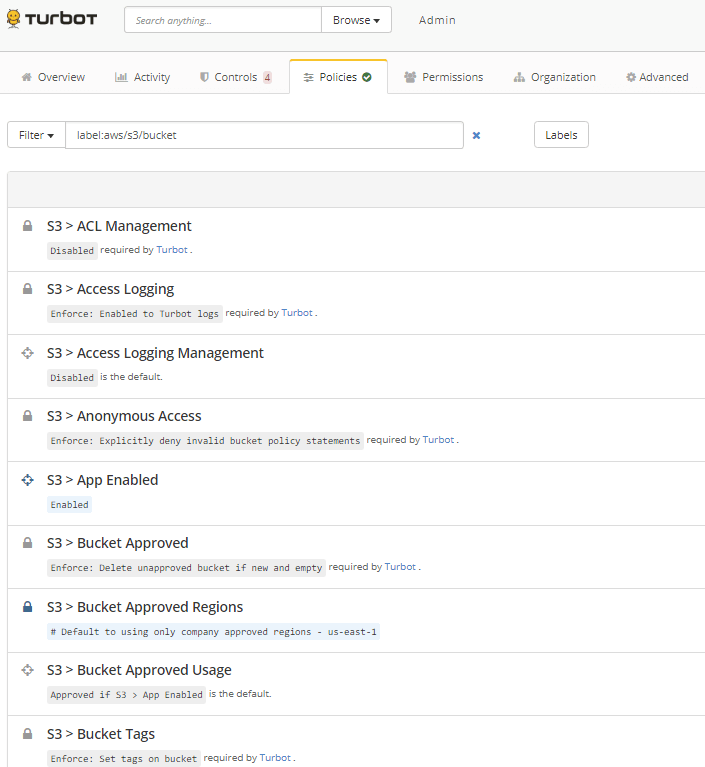
Some examples of Turbot Guardrails AWS S3 Guardrails that explicitly deny anonymous and public access, and remediate misconfigured S3 buckets that expose data to public unnecessarily:
- Enable / Disable AWS S3 from being used by users (prevents rights to S3 unnecessarily to teams who do not need to use S3)
- Prevent rights to manage Access Control Lists (disable rights to make objects public facing)
- Prevent rights to manage CORs (disable rights to manage cross-origin configurations)
- Explicitly deny anonymous access on buckets
- Explicitly deny cross account access (or only allow trusted accounts)
- Restrict access to buckets from specific CIDRs
In addition to helping organizations ensure their data is safe, Turbot Guardrails helps automate other operation & security best practices; examples:
- Enforce Access Logging on buckets
- Allow only specific regions for buckets
- Automatically apply tagging schemes
- Ensure DNS compliant bucket names
- Ensure Encryption at Rest (SSE, KMS, etc.)
- Ensure Encryption in Transit
- Ensure Versioning
Note: Turbot recommends that enterprise customers set these policies in Turbot Guardrails as a standard default to protect themselves globally across all of their buckets. Exceptions to specific buckets or collection of buckets can then be done after internal change control and review of the specific use case.
Our next major event is AWS re:INVENT in Las Vegas from November 27th - December 1st. We can't wait to see you there! Until then, reach out to connect with us for a demo on Turbot Guardrails latest features and solutions.
