CfnCluster ("CloudFormation cluster") is a framework that deploys and maintains High Performance Computing (HPC) clusters on Amazon Web Services (AWS). Developed by AWS, CfnCluster facilitates both quick start proof of concepts (POCs) and production deployments for various HPC workloads. CfnCluster supports many different types of clustered applications and can easily be extended to support different frameworks.
Turbot Guardrails fully supports CfnCluster by automating various operational and security controls:
- Managing whitelisting policies for specific AWS services to be used with CfnCluster
- Least privileged CfnCluster IAM roles & users permissions
- Restrict only CfnCluster AMIs to be used
- Turbot Linux Guardrails to harden the Operating System (OS) tier, sync users from Active Directory, manage patching, and environment variables.
This allows HPC application users to quickly spin up CfnCluster without spending anytime to manually configure security and operational controls on the infrastructure, operating system, and application configuration tiers. As HPC environments can be transient (constantly spin up and down to run jobs), these Turbot Guardrails provide accelerated DevOps practices for teams to spend less time managing CfnCluster setup and configurations, and more time running value-added HPC workloads.
CfnCluster Turbot Guardrails Options
Whitelist only CfnCluster AWS Services
CfnCluster uses a wide range of AWS Services, all orchestrated through CloudFormation. Turbot Guardrails offers IAM guardrails to whitelist specific AWS Services, AMIs, RDS Engine Types, etc. When using Turbot Guardrails IAM, users are prevented from using any services not enabled / whitelisted. These preventative controls will ensure only these services can be used in the AWS Account to prevent any unwanted services from being used. The following guardrail options must be enabled to use CfnCluster:
- AWS Core Enabled (includes):
- CloudFormation
- CloudWatch
- IAM
- EC2 Enabled (includes):
- Autoscaling
- EBS
- EC2 Instances
- DynamoDB Enabled
- KMS Enabled (optional if requiring encryption for EBS volumes)
- S3 Enabled
- SQS Enabled
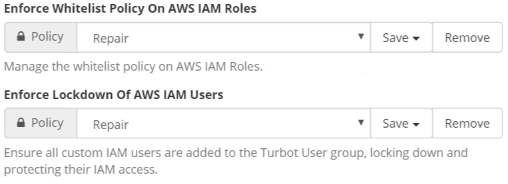
Lockdown Policy Access for CfnCluster Users & Roles
CfnCluster requires the use of two separate roles / users:
- CfnClusterUser - Used by the CfnCluster scripts to run CloudFormation and create resources.
- CfnClusterInstance - Used by CfnCluster EC2 nodes.
Turbot Guardrails will continuously enforce lockdown configurations on these users and roles in AWS to the permissions available by the whitelisting policies configured in that AWS account. These lockdown policies do not impact its operation since its permission requirements are within Turbot Guardrails limits.
Turbot Guardrails will automatically enforce these lockdown policies on all users and roles when the Enforce Whitelist Policy On AWS IAM Roles & Enforce Lockdown Of AWS IAM Users guardrails are set to Repair any misconfigured policies.
Guardrails for CfnCluster AMIs, Operating System & User Management
CfnCluster has two types of instances that run in a VPC:
- Launcher instance - Human login to use CfnCluster commands. Uses the CfnClusterUser role.
- Cluster instances - Managed by CfnCluster. Use the CfnClusterInstance role. Turbot Guardrails recommends the use of your standard Linux AMI for the launcher instance, including Turbot managed Linux.
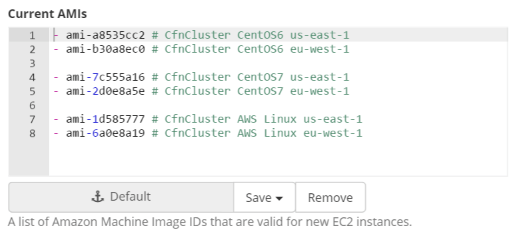
AMI Whitelisting
Turbot Guardrails can enforce only specific AMIs are allowed to be provisioned in one or many AWS Accounts. Administrators can define a list of AMIs allowed for an account by using the Current AMIs option in Turbot Guardrails. Example for restricting only to CfnCluster AMIs in the AWS Regions us-east-1 and eu-west-1 AWS regions:
Linux OS Hardening Guardrails for CfnCluster
The CfnCluster launcher can run multiple flavors of Linux; Turbot's Linux Guardrails can be used to automatically manage Linux OS Center for Internet Security (CIS) Level benchmarks hardening, user management sync from Active Directory (AD), etc. Simply start a Linux instance with the turbot Guardrails SSH key pair and the CfnClusterUser IAM Role described above. Turbot Guardrails will detect when the instances are provisioned and continuously enforce the Linux hardening and user management configurations.
