Turbot Guardrails provides governance for a number of AWS security, identity, and compliance products. Turbot has recently expanded our coverage for AWS Security Hub announced today during the AWS Reinvent 2018 Keynote. Turbot Guardrails delivers public cloud governance for the enterprise with automation that verifies your cloud infrastructure is secure, compliant, scalable and cost optimized. Turbot Guardrails policy model helps enterprises validate that AWS Security Hub is setup and configured according to defined enterprise policies to manage security alerts and compliance checks centrally across AWS accounts and workloads. Turbot Guardrails automatically sends security and compliance event details to AWS Security Hub in real-time to further enhance visibility for customers to have a single pane of glass of their AWS and Turbot Guardrails event details in AWS Security Hub.
Turbot Guardrails Enables AWS Security Hub in Multiple Accounts
Turbot Guardrails allows you to enable / disable AWS Security Hub in multiple AWS accounts. This will block users from managing AWS Security Hub per account and allow central configuration management to be enforced globally or managed through exceptions per account and per instance. Turbot Guardrails can enable / disable specific regions allowed for AWS Security Hub resources.
As part of Turbot Guardrails identity engine, enterprises can easily assign AWS Security Hub role based access controls (RBAC) and identity policies consistent with other Turbot managed policies. In addition, Turbot Guardrails RBAC policies can be applied as time-based grants.
Turbot Guardrails and Security Hub Findings
Turbot Guardrails has the ability to take Turbot Guardrails controls and transform them into AWS Security Hub findings. To achieve this, Turbot Guardrails needs to convert the format of the control data to that of the AWS Security Finding Format (ASFF). The following explains that transformation in detail.
| ASFF Field | Turbot Use of Field |
|---|---|
| Id | "turbot:" + UUID |
| GeneratorId | The URN of the Turbot Guardrails alarm. |
| ComplianceStatus | Maps to the control state. PASSED if the control is in an OK or SKIPPED state. FAILED if the control is in an ALARM or ERROR state. NOT_AVAILABLE for all other control states. |
| Title | Title from the Turbot Guardrails notification message. |
| Types | Currently limited to "Cloud Compliance and Best Practices Checks". |
| Description | Description from the Turbot Guardrails notification message. |
| ProductFields | Turbot Guardrails uses this field to pass in the alarm URN, the resource URN, and the process URN. |
| RecordState | ACTIVE for all findings with a ComplianceStatus of FAILED or NOT_AVAILABLE. All findings with a ComplianceStatus of PASSED are archived. |
| Severity | Default values are 5.0 for product and 50 for normalized. Currently not configurable. |
Findings are only generated for controls with a ComplianceStatus of FAILED or NOT_AVAILABLE. When the ComplianceStatus of a finding changes to PASSED, the finding it archived.
A way to gauge how many findings Turbot Guardrails would import to AWS Security Hub is to look at the write metrics for the Turbot Guardrails notifications AWS DynamoDB Table, as this varies from environment to environment.
How it Works
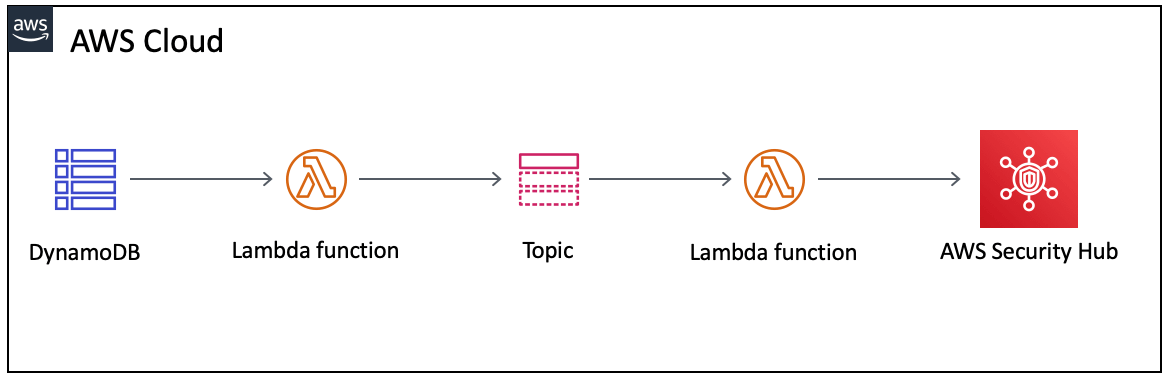
The image above shows the architecture of how Turbot Guardrails integrates with AWS Security Hub. Turbot Guardrails notifications are stored in a AWS DynamoDB table. Using AWS DynamoDB streams, an AWS Lambda function is triggered to transform those notifications and send them to an AWS SNS topic. Next, an AWS Security Hub specific AWS Lambda function is invoked and transforms the Turbot notification AWS SNS message to the AWS Security Hub finding format and imports the finding into AWS Security Hub.
Contact us to learn more about Turbot Guardrails for AWS Security Hub or schedule a demo to see how Turbot Guardrails can fully automate Cloud Governance for your organization.
