Enterprises often are held back from quickly progressing their cloud adoption due to budget constraints. Turbot believes you should never have to sacrifice innovation due to budget limitations, defining a clear approach to governing your cloud spend becomes essential to avoid risk of overspending. Gartner estimates that organizations that have done little to no cloud optimization are overspending by 70% or more. (Three Moves for CIOs to Lower Business Costs With Cloud)
Turbot Guardrails cloud governance platform ensures your cloud spending is under a controlled budget by preventing or optimizing costly configurations. With simple point-and-click policies, you can instantly discover resource changes, clean up unused resources, remove or stop resources based on budget thresholds, and reduce access based on budget limits. Turbot Guardrails cost controls have saved up to 90% in Fortune 1000 customers' development environments, freeing up budget for business-critical cloud deployments. Turbot Guardrails governance controls start at $0.05 per monthly control, preventing large costly actions, saving you thousands in cloud usage for a fraction of the cost.
Contextual Awareness of Your Cloud
In order to gain control over your cloud budget, you need to understand and be aware of changes occurring across your environment. Turbot Guardrails provides a Cloud Configuration Management Database (CMDB) for the cloud age, which discovers everything and is immediately contextually aware of your environment. Turbot Guardrails instantly discovers, types and categorizes new resources, captures detailed configuration drift with an audit trail of existing resource changes, and provides real-time searchable dashboards for teams to personalize their view of the environment.
Turbot Guardrails Cloud CMDB can enforce resource hierarchy positioning, grouping, and organizational policies to ensure your cloud resources are appropriately named and tagged, along with ensuring the cloud resource is appropriately running in the correct account, region, network, etc. As changes occur, Turbot Guardrails automatically calculates the correct organizational policies based on the conditions of the resource. Turbot Guardrails can track these changes in its CMDB audit trail, raise alarms on issues, or be set to enforce corrections immediately as they occur.
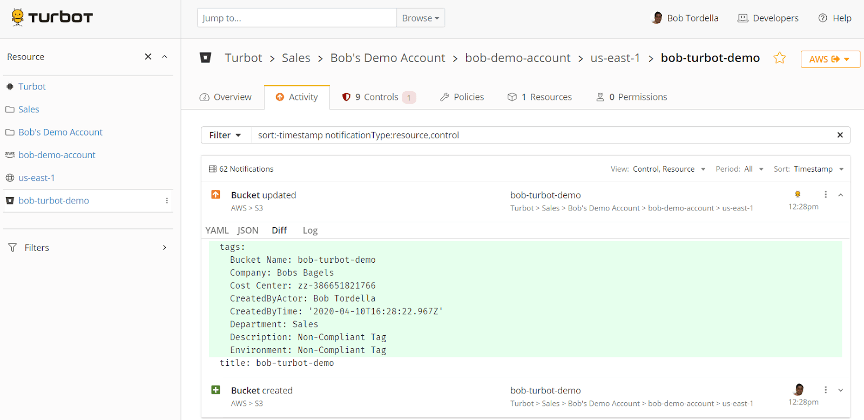
Turbot Guardrails activity history showing the user created a resource, Turbot then immediately applied the approved tags
With Turbot Guardrails CMDB you can identify what you have and who owns it. Tag resources with user ownership, cost center information, and created time to give you a better handle from where the spend is coming. This information can be used to track usage through detailed billing reports.
Manage within your Cloud Budget
Turbot Guardrails Budget Controls can discover your current and forecasted spend against a planned target and take appropriate actions to help control cost based on thresholds. All cloud current and forecasted spend is tracked through the Turbot Guardrails CMDB so you can visualize the changes in your activity audit trail. Turbot Guardrails allows you to set budgets per account and alert on thresholds when the spend is trending out of alignment with the budget.
Turbot Guardrails defines named Budget States which are used to enforce policies and controls based on Targets and Thresholds that are set. Targets define the allowed spend for the account, while Thresholds will calculate which Budget State will be set. Example below:
| State | Threshold | Description / Intent |
|---|---|---|
| Shutdown | 500% | Budget is completely spent, or trending significantly over. No more money is available. All spending must cease, even if it results in degraded service |
| Critical | 300% | Budget is completely spent, or trending significantly over. Urgent action is needed to reduce spend. |
| Over | 125% | Current or forecast spend exceeds the budget target. |
| On target | 100% | Current and forecast spend are in line with the budget target. No action is required |
| Under | 10% | Current and forecast spend are lower than projected |
| Unused | N/A | The current and forecast spend is so low that it appears that this account may not be in-use |
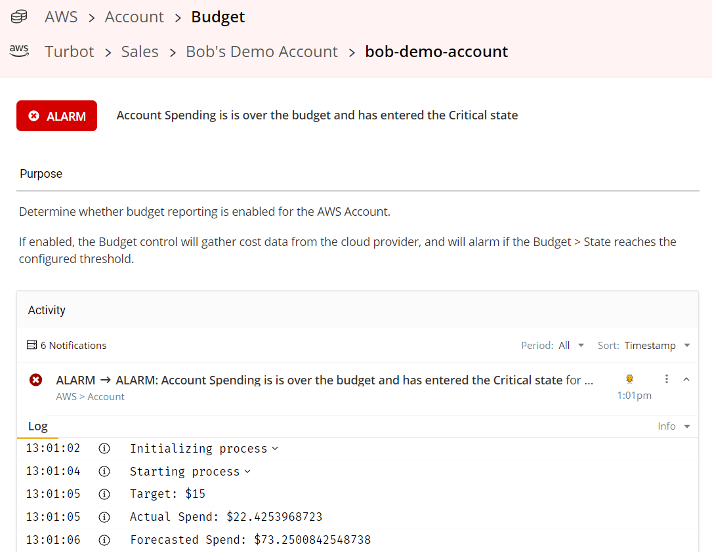
If you exceed your Target, Turbot Guardrails will alarm providing Budget State context. Additional Details on Actual Spend, Forecasted Spend and Target Spend are visible in the Control Detail
Prevent Costly Cloud Usage
Turbot Guardrails cloud governance cost controls can be leveraged to prevent costly user actions from occurring at any level in your organization. These preventative controls may be set due to budget constraints, preventing costly actions, preventing a compliance or security risk, or avoiding an operational issue that may occur. Below are examples of preventive controls from a cost perspective.
Turbot Guardrails Service Boundary allows you to prevent teams from using costly services without approved use (e.g. Amazon Redshift, Azure AKS, GCP BigQuery, etc)
Cost of services per cloud region can vary as much as 60%. Using Turbot Guardrails Region Boundary, you can prevent access to unapproved, costly Regions.
Turbot Guardrails Permission Boundary enables or disables specific actions (e.g. managing ACLs on a storage bucket) which may cause a costly outcome such as a data breach. By locking down permissions, you protect your data from unnecessary exposure before it occurs.
Using Turbot Guardrails Budget Boundary, you can restrict APIs based on the budget state (When the current spend exceeds the defined threshold), preventing further costly mistakes.
Turbot Guardrails Configuration Boundary allows you to enable or disable cloud configurations (e.g specific sizes of Disks, Compute Instance Types, BD Engines, Marketplace Images, etc.), preventing teams from provisioning costly environments that may be unnecessary for use cases in the environment.
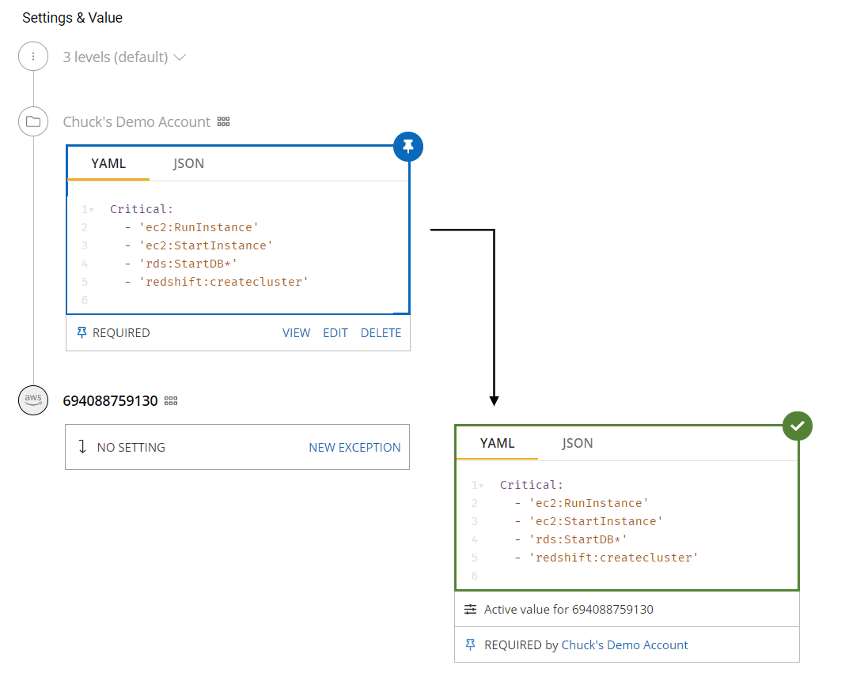
Example of setting Budget Boundary Policies for what API permissions will be restricted when the account is in "Critical" Budget State
Optimize Cloud Usage
There is a balance of preventative and corrective measures to find the right balance between agility and control. There are cases where you cannot prevent a costly action from occurring when resources may gradually scale over time, application teams are purposely given more agility and freedom to innovate through self-service, etc. You can use Turbot Guardrails governance controls to automate corrective measures on costly configurations. Here are some examples:
Inactive Resources
Inactive Use refers to Cloud Accounts and Resources becoming unused or orphaned for varying reasons, for example a Sandbox project left open and unintended because key project team members are reassigned or leave the project, or volumes are left unattached after an instance decommission, etc. Turbot Guardrails can be used to identify and automatically clean up resources to optimize the environment.
- Age: time lived duration. Clean-up resources if they have been
provisioned for X days.
- Last Used / Last Modified: time since last change or use of resource.
Clean-up resources that are intended to be used or changed often. If no
usage or modified activity occurs over X days then alarm or remove.
- Unallocated / Empty / Status: whether the resource is in use based on allocation, if empty or with a specific operational status. Turbot Guardrails can clean-up resources if they are deemed unused.
- Age: time lived duration. Clean-up resources if they have been
provisioned for X days.
Instance Scheduling across AWS, Azure, GCP, and applicable cloud services stop instances on a planned schedule. For example, by shutting down Sandbox and Development environments on nights and weekends, you can save over 75% of runtime costs.
Example of EC2 > Instance > Active controls in "OK" Control State, showcasing examples of Active policies that can be set based on Age, Attached, Budget, and Last Modified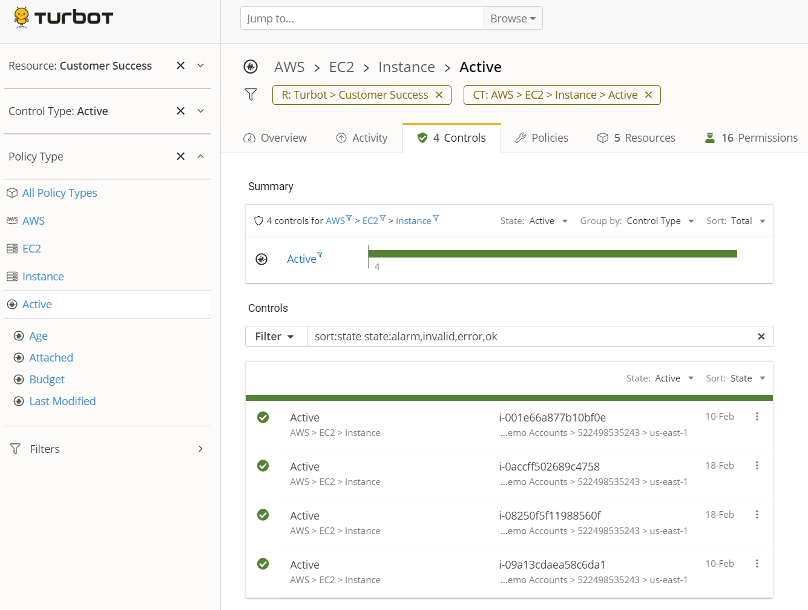 Example of an Instance Schedule Control initiated, executed, and then has Stopped the Instance
Example of an Instance Schedule Control initiated, executed, and then has Stopped the Instance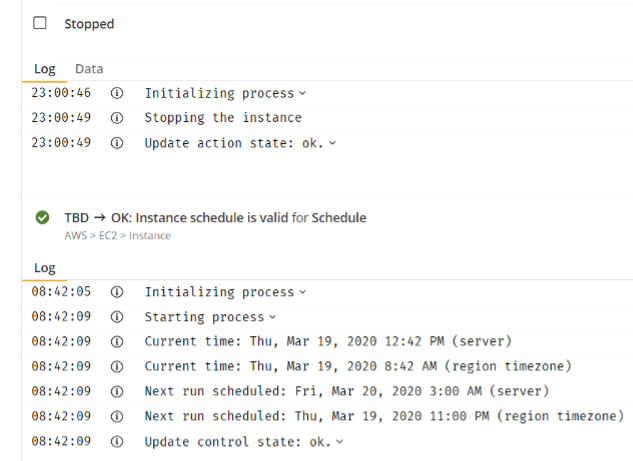
Unapproved Resources
- Unapproved Conditions allow you to set conditions that are approved.
Turbot Guardrails can be used to identify and automatically clean up resources
to optimize the environment, examples:
- Disk Size (e.g. >100GB) over an unapproved size
- Instance Type used (e.g. c*, xlarge, etc.) is over an unapproved size
- Expensive DB licensing not approved by default (e.g. Oracle EE) without
exception
- Specific Images are not approved for use in x Account(s)
- Specific Marketplace items or publishers are not approved
- Duplicate resources like log streams, trails, etc.
- Resources provisioned in the wrong region
- Disk Size (e.g. >100GB) over an unapproved size
- Usage Limits raise awareness of how many resources of the applicable service can be used in the environment, and what is the current consumption against the limit.
- Budget Thresholds remediate costly resources when budget thresholds are met. Turbot Guardrails can raise alarms or enforce changes immediately to prevent and remediate costly mistakes. For example you have your AWS > EC2 > Instance > Approved policy set to "Enforce: Delete unapproved if new". For EC2 there are other conditions that can be set based on AMI, Instance Type, Public IP, Regions, etc. Budget is an additional condition that can be set, e.g. "Unapproved if Budget > State is Critical or higher"
Conclusion
The above scenarios are just examples of how Turbot Guardrails can keep you under budget and in control of your cloud usage. Beyond our cost controls, Turbot Guardrails full-stack governance platform automates discovery and remediation of your organization's compliance, security, and operational objectives as well with 6000+ OOTB controls. Turbot Guardrails platform can be extended with your own configurations and customizations providing ultimate flexibility to leverage our CMDB, Policy and Identity Engines to meet your organizational requirements.
To know more about how your business can regain control over your cloud budget, read our "Cloud Cost Controls" whitepaper. Get started with your Turbot Guardrails Free Trial today for a complimentary cost assessment!
