This month, Amazon announced the availability of S3 default encryption. Default encryption is available as a property on the S3 bucket when it is created, through the AWS REST API, or through the AWS CLI. The default setting available from Amazon for S3 default encryption is "None", and this must explicitly be enabled at, or after, the time that the bucket is created. When established, S3 default encryption will ensure that any unencrypted objects presented to S3 are encrypted via the specified method. Amazon S3 default encryption can be configured on each bucket using either Amazon S3-managed keys (SSE-S3) or AWS KMS-managed keys (SSE-KMS). For large organizations, ensuring that these properties are applied universally and consistently can be very challenging, especially considering that new workloads and data are being added to the cloud every day.
To further support Amazon's efforts for rolling out S3 default encryption, Turbot Guardrails has released additional guardrails to configure S3 default bucket encryption, and will also continue to manage encryption at rest bucket policies. Turbot Guardrails builds further upon default encryption by enforcing encryption at rest through AWS S3 Managed Keys (SSE-S3), AWS KMS Managed Keys (SSE-KMS), or customer managed KMS keys. Encryption at rest for S3 objects can be enforced using Turbot Guardrails S3 Encryption at Rest option. Turbot Guardrails will automatically update S3 bucket policies and default encryption settings to enforce the option when enabled.
Turbot Guardrails S3 Encryption at Rest option has the ability to specify multiple options for encryption. For example, setting the option to "Enforce: AWS KMS or higher" explicitly denies AWS SSE, and ensures that any unencrypted objects will be encrypted with AWS KMS. Setting the option instead to "Enforce: AWS SSE or higher" permits the use of AWS SSE or AWS KMS when uploading an object, and ensures that at minimum, the object is encrypted with at least AWS SSE. Turbot Guardrails enforces these settings through a combination of values applied to the bucket's Default Encryption properties, and application of bucket policies to give you configurable choices on how to protect your S3 buckets. A matrix of these options is provided at the end of this article.
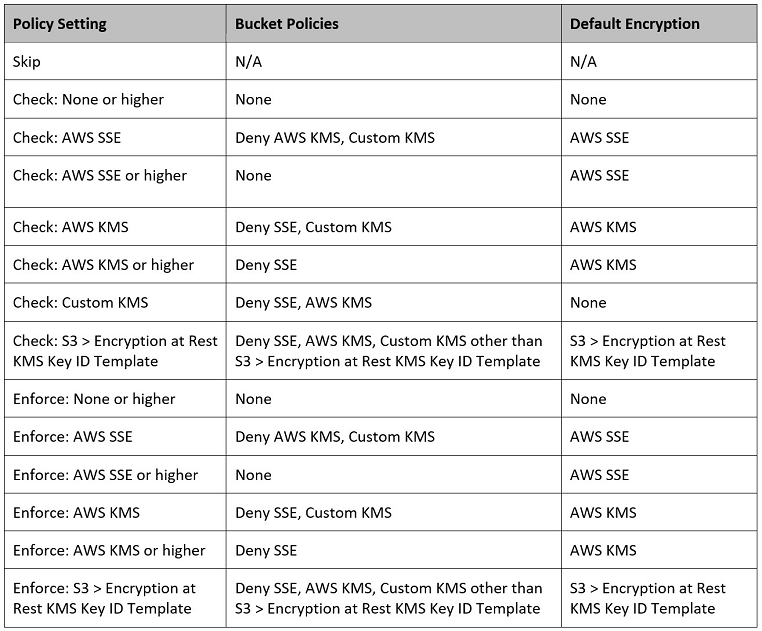
Most important, when placed in Enforce mode, Turbot Guardrails ensures that the selected S3 default encryption and encryption at rest bucket policies are applied automatically and consistently when S3 buckets are created - every time. The following table details the options available for Turbot Guardrails Encryption at Rest policy.
- "Skip" instructs Turbot Guardrails not to review any of the settings for this policy.
- "Check" instructs Turbot Guardrails to evaluate whether the settings are in place on an S3 bucket, and create an alarm if not set properly.
- "Enforce" instructs Turbot Guardrails to evaluate and modify any property or policy on the S3 bucket that is not in compliance with the configuration noted in the table below.
-- | Policy Setting | Bucket Policies | Default Encryption | | ---------------------------------------------------- | ------------------------------------------------------------------------------------ | ------------------------------------------- | | Skip | N/A | N/A | | Check: None or higher | None | None | | Check: AWS SSE | Deny AWS KMS, Custom KMS | AWS SSE | | Check: AWS SSE or higher | None | AWS SSE | | Check: AWS KMS | Deny SSE, Custom KMS | AWS KMS | | Check: AWS KMS or higher | Deny SSE | AWS KMS | | Check: Custom KMS | Deny SSE, AWS KMS | None | | Check: S3 > Encryption at Rest KMS Key ID Template | Deny SSE, AWS KMS, Custom KMS other than S3 > Encryption at Rest KMS Key ID Template | S3 > Encryption at Rest KMS Key ID Template | | Enforce: None or higher | None | None | | Enforce: AWS SSE | Deny AWS KMS, Custom KMS | AWS SSE | | Enforce: AWS SSE or higher | None | AWS SSE | | Enforce: AWS KMS | Deny SSE, Custom KMS | AWS KMS | | Enforce: AWS KMS or higher | Deny SSE | AWS KMS | | Enforce: S3 > Encryption at Rest KMS Key ID Template | Deny SSE, AWS KMS, Custom KMS other than S3 > Encryption at Rest KMS Key ID Template | S3 > Encryption at Rest KMS Key ID Template |