Using tags for cost allocation, to track resource ownership, and automate operational actives has always been a Turbot Guardrails recommended best practice; however, manually managing thousands of tags across accounts, resources and services is an inconsistent and error prone process. Effectively enforcing tag standards across an Enterprise requires tooling that works across multiple cloud environments (e.g. AWS, Azure, GCP), cloud accounts, cloud services/resources, users, and varying context per application use case.
To assist our customers with managing tags centrally, applying guardrail enforcements, and enforcement of naming schemes across a multiple cloud ecosystems; Turbot is pleased to launch our New Tag Management Guardrails!
Turbot Guardrails Tag Management
Tag Management allows teams to configure centralized tagging and enforce specific key/value pairs across Turbot Guardrails accounts and cloud resources. Tags are defined in templates which provide flexible naming schemes for keys and values. These templates can be defined for groups of accounts, across all resources in a single account, across all resources in an individual service (e.g. EC2) or individually set for a particular resource (e.g. RDS Instance, Redshift Cluster, S3 Bucket, etc.).
These options are managed by Turbot Guardrails just like other guardrails:
- Skip (do not apply tags)
- Check (create an alarm if the tags are not set properly)
- Enforce (automatically enforce naming schemes)
When enforcing tags, if a tag is modified and differs from the definition in the template, Turbot Guardrails will update this tag in real-time to match the template definition.
Turbot Guardrails Tag Management in Action
Getting Started
Each cloud service resource has 2 options for managing tags:
- Tags Template - Define the key/value pairs for tags.
- Tags - Set whether Turbot Guardrails checks or enforces the tags defined in the tags template.
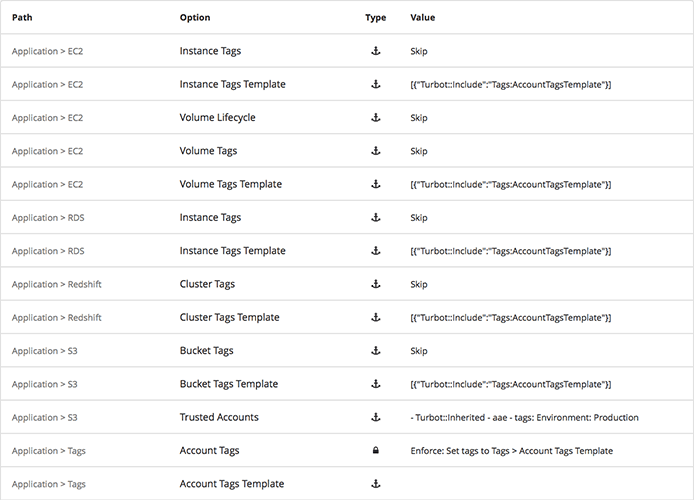
The Tags option must be set to Enforce in order for Turbot Guardrails to manage tags, which includes creating, updating, and deleting tags according to the tags template option.
Setting Custom Tag Templates
Each resource's tag template is a YAML list of key/value pairs that admins can simply set through their Turbot Guardrails Options at any tier of the hierarchy. Tags can include a mixture of static content, Turbot Guardrails metadata, and environment attributes from their cloud resources e.g. EC2 Instance data type
Various scenarios can be applied with varying context logic to enforced Key:Value pairs:
Use Turbot Guardrails Account info, AWS Region, and EC2 Instance Data
{% raw %}- Company: Bob's Bagels{% endraw %}
{% raw %}- Cost Center: "zz-{{ account.id }}"{% endraw %}
{% raw %}- InstanceId: "{{ InstanceId }}"{% endraw %}
Allow any value except null, set to "Non-Compliant" if out of bounds
{% raw %}- Description: "{% if TagsMap['Description'] in [''] %}{{ TagsMap['Description'] }}{% else %}Non-Compliant{% endif %}"{% endraw %}
Enforce selection of values, set to "Non-Compliant" if out of bounds
{% raw %}- Environment: "{% if TagsMap['Environment'] in ['Dev', 'QA', 'Prod'] %}{{ TagsMap['Environment'] }}{% else %}Non-Compliant{% endif %}"{% endraw %}
Copy tags from other services; e.g. auto tag EBS volumes with EC2 tags
{% raw %}- Turbot::Include: EC2:VolumeTagsTemplate{% endraw %}
Turbot Guardrails Managed Tags
Turbot Guardrails also has pre-defined tagging options to manage Hostnames, DNS Records, CreatedBy, ModifiedBy, etc. that can be automatically set by Turbot Guardrails. Examples:
EC2 Instances
- turbot:CreatedBy - Friendly name of the user who created the instance, e.g., "John Bell jbell@example.com".
- turbot:CreatedByUrn - The Turbot Guardrails URN of the user who created the instance.
- turbot:CreatedTimestamp: Date and time the instance was created.
EBS Volumes
- turbot:DetachedTimestamp - Date and time of when the volume was last detached. If the time is unknown, it will be set to when the guardrail is run next. This tag will be removed if the volume is attached.
- turbot:LastInstanceId - Instance ID of the last known attached instance. This tag will be removed if the volume is attached.
Tag Automation in Action
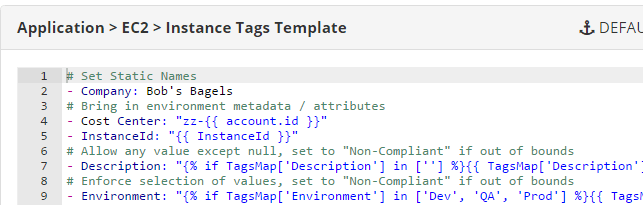
Example of Tags defined in a YAML list for custom EC2 Naming Template
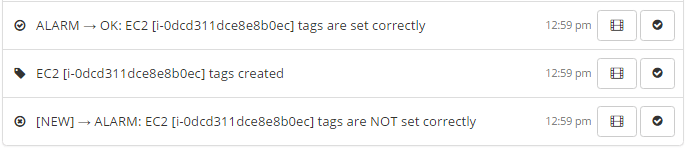
Activity history of an instance being created, Turbot Guardrails detecting it in seconds, and enforcing Tags:
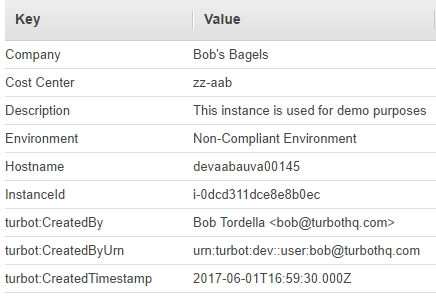
Tags automatically applied to the EC2 instance in real-time:
We look forward to seeing new use cases of how our customers will leverage these new Tag Management features. Contact us to schedule a demo of Turbot Guardrails Tag Management Guardrails.
