Turbot Guardrails now supports custom S3 bucket policies and has added new guardrails to restrict anonymous and cross-account bucket access. Users with AWS/S3/Admin permissions can create, update, and delete bucket policies for all buckets in their account (except for the regional Guardrails logging buckets).
Adding Bucket Policies
Here's how you can add a custom bucket policy to a bucket in an account that has the "S3 > Encryption at Transit" option enabled.
Start by selecting the S3 bucket, expand Permissions, and click on Edit bucket policy (or Add bucket policy):
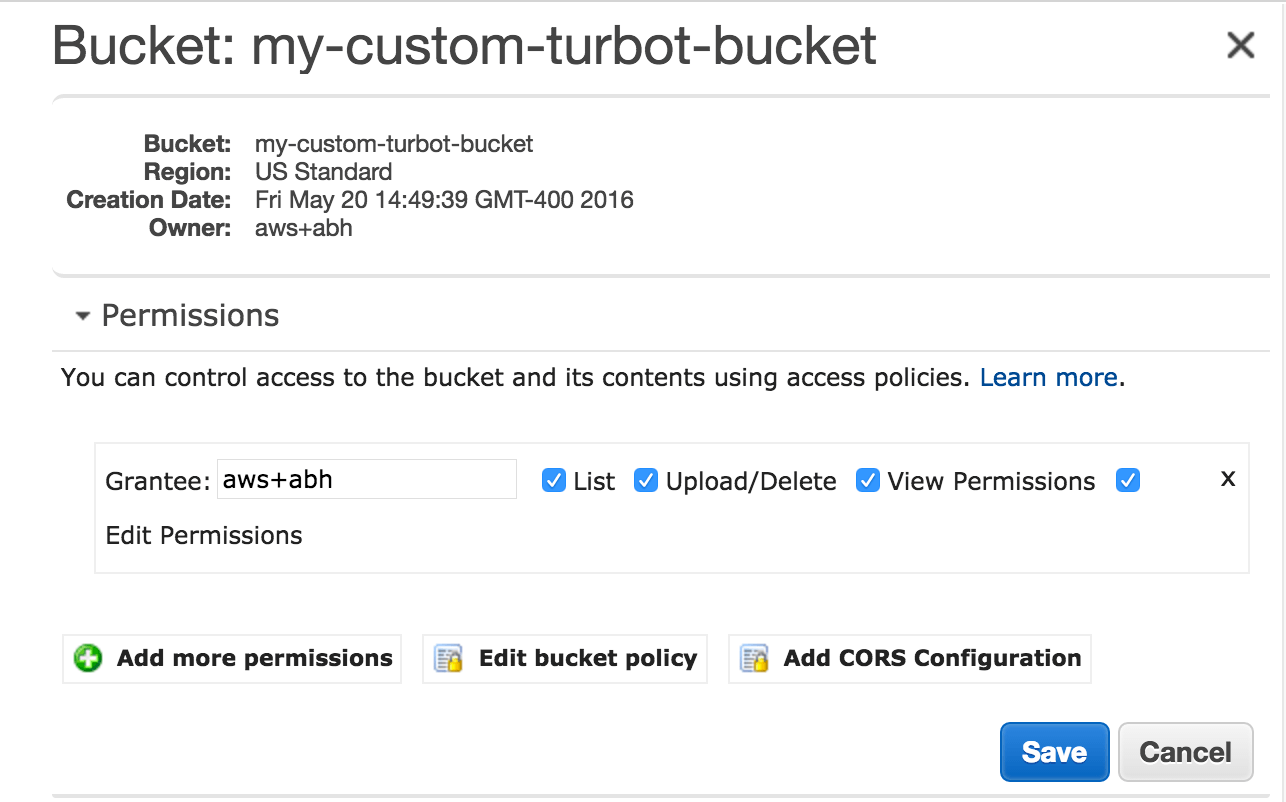
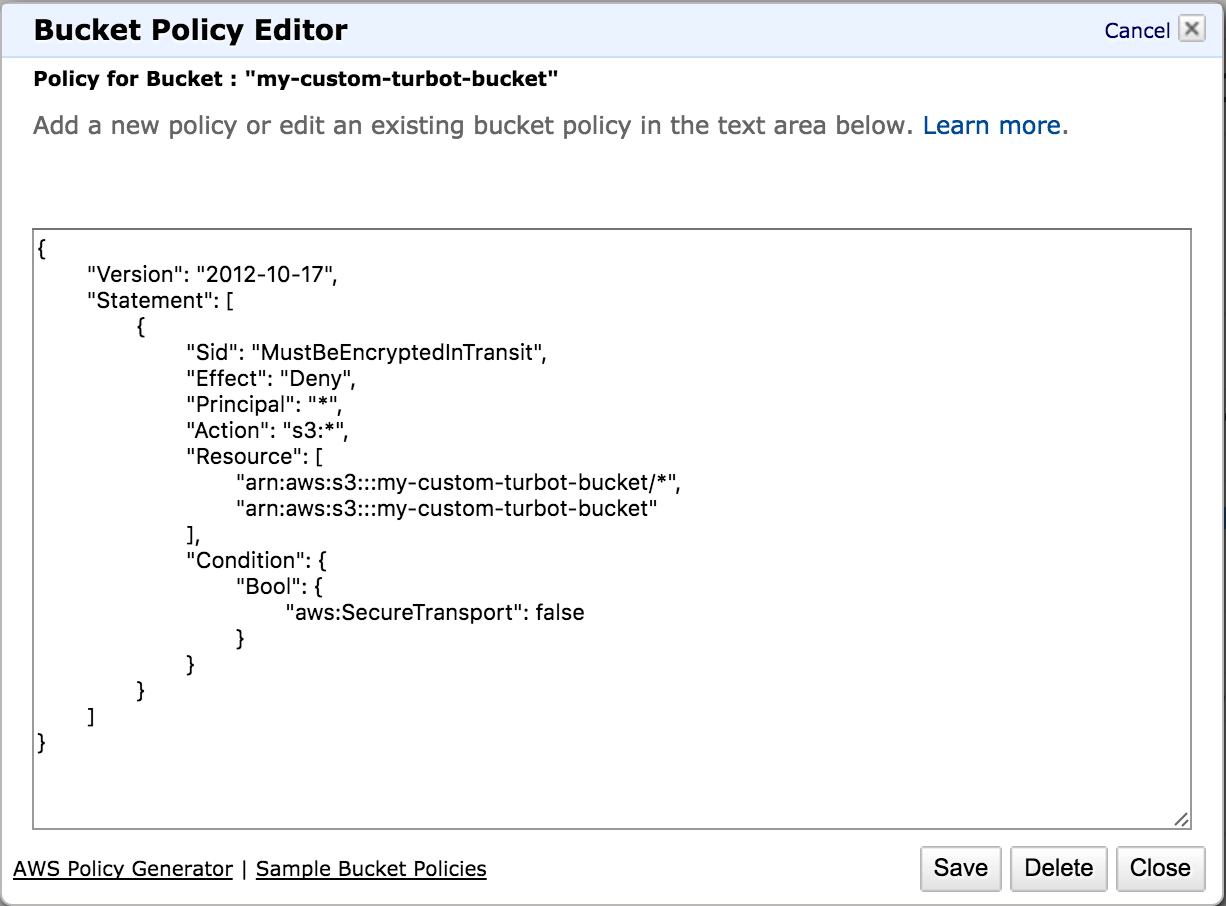
You should already see the bucket policy enforcing encryption in transit:
Add your own statements to the bucket policy and then Save your changes:
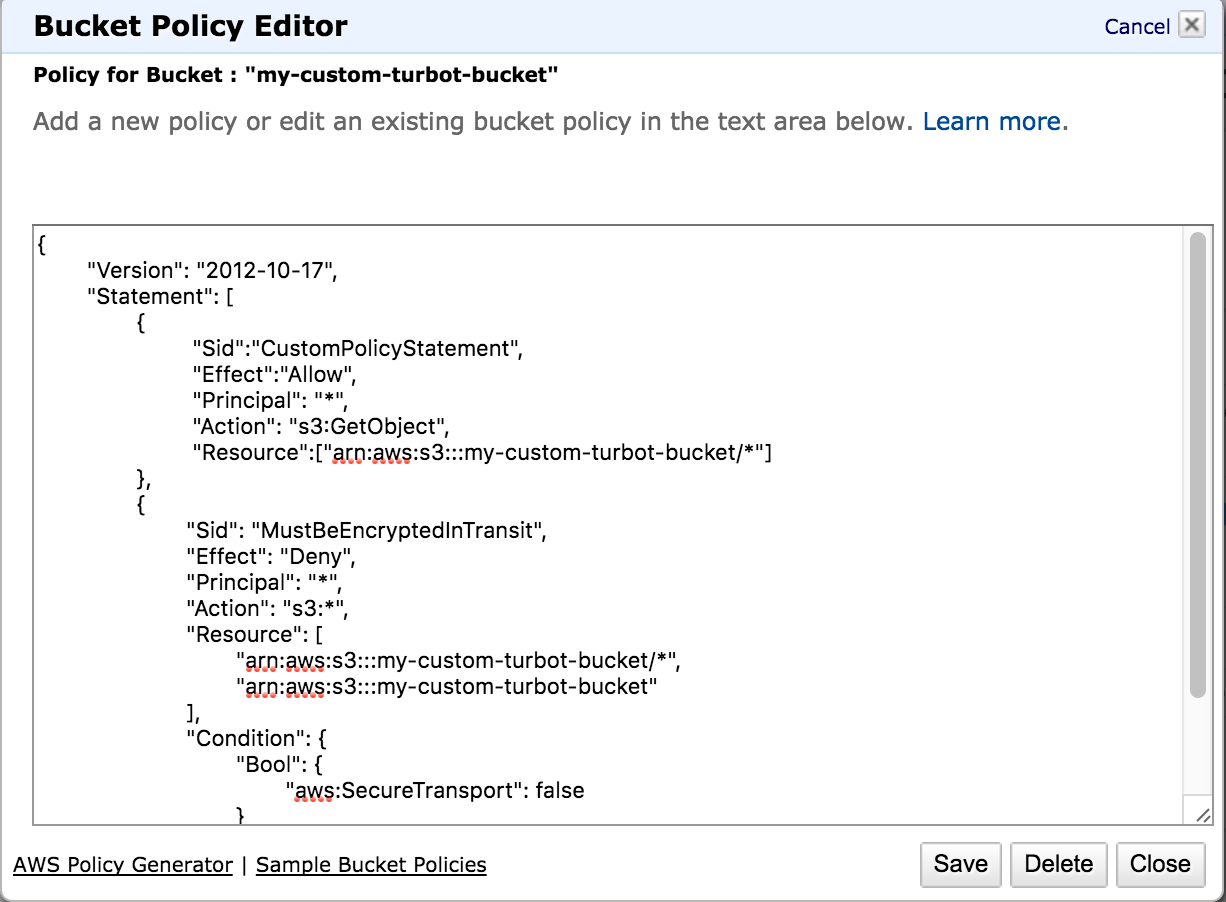
Example bucket policies are available from AWS to help users get started.
Anonymous and Cross-Account Access Guardrails
Cluster administrators can restrict anonymous and cross-account access through S3 options:
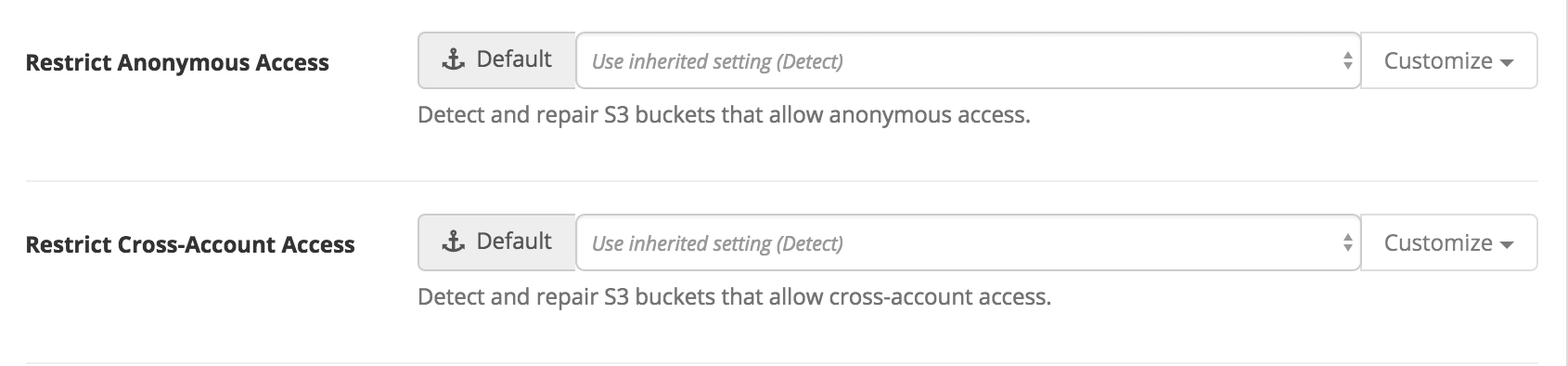
If either option is set to Repair, any prohibited access will be denied and the policies will need to be cleaned up manually.
Turbot Guardrails recommends restricting anonymous and cross-account access unless there is a specific requirement to allow them.
