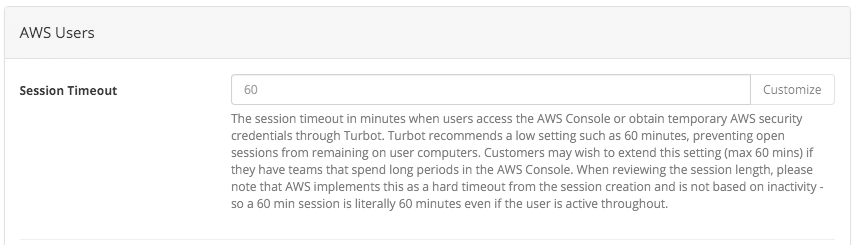
In its continuing efforts to simplify AWS cloud management and operations, Turbot Guardrails has added an option "AWS Users > Session Timeout" allowing Cluster Administrators to set the preferred AWS user session length in minutes. As always, this option can be a policy or a recommendation and managed at a Cluster or Account level.
When accessing the AWS Console, or requesting temporary security credentials, users are always subject to a hard session timeout from AWS. This timeout is set by the DurationSeconds field in calls to STS GetFederationToken.
Unfortunately AWS implements this as a hard timeout from the start of the session, completely unrelated to activity. This means users are sometimes frustrated by AWS console logouts while they are in the middle of working sessions.
Until now, this session has always been 60 minutes in Turbot Guardrails - long enough to do useful work, but genearlly short enough to avoid unauthorized users leveraging an open session on an unattended computer.
Turbot Guardrails recommends the 60 minute session length, and has maintained that as our default. AWS has a default session length of 12 hours (720 minutes), so that may be a preferred setting for your users. The maximum allowed is 36 hours (2160 minutes).
For a full demo of all the ways Turbot Guardrails can enhance and support your cloud team, please get in touch.
